analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
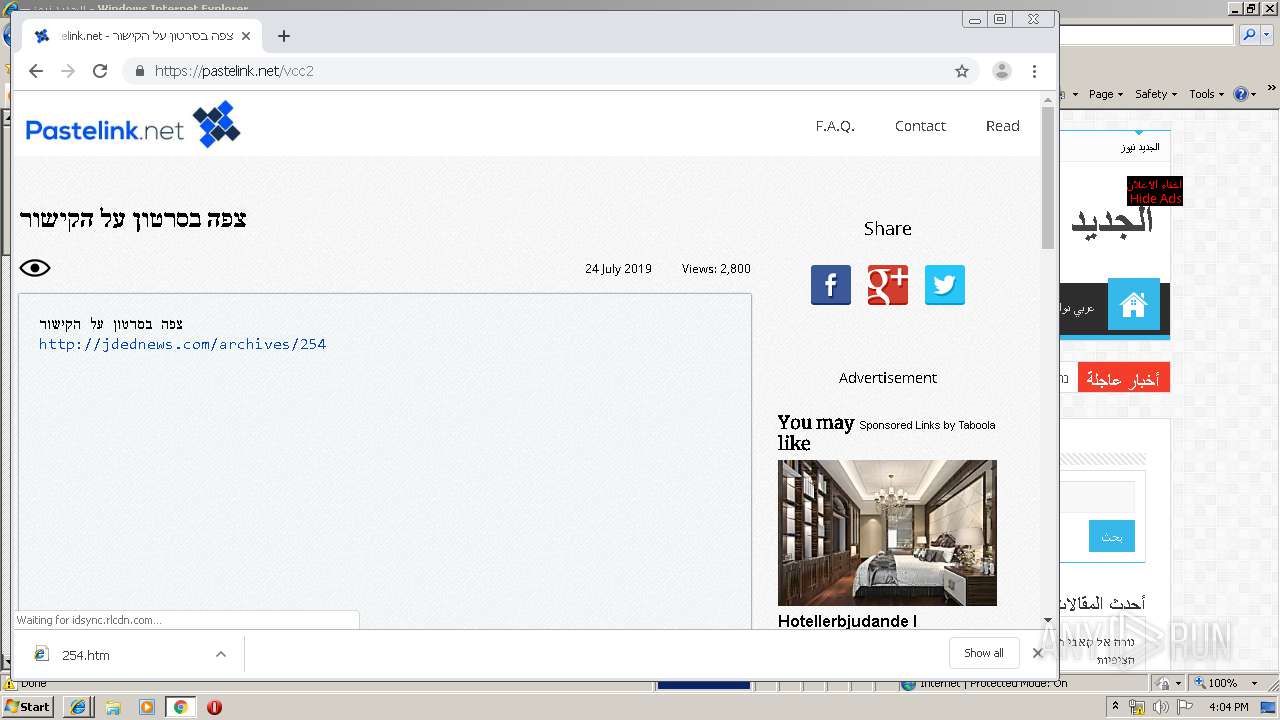
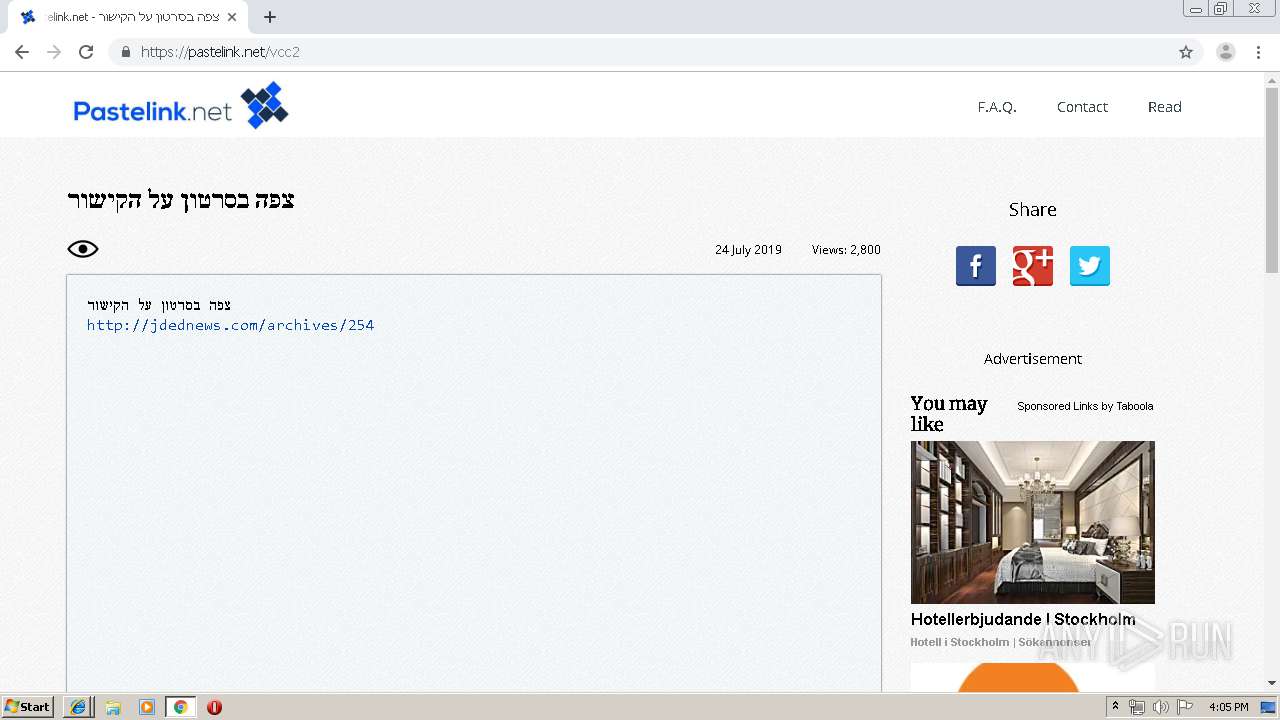
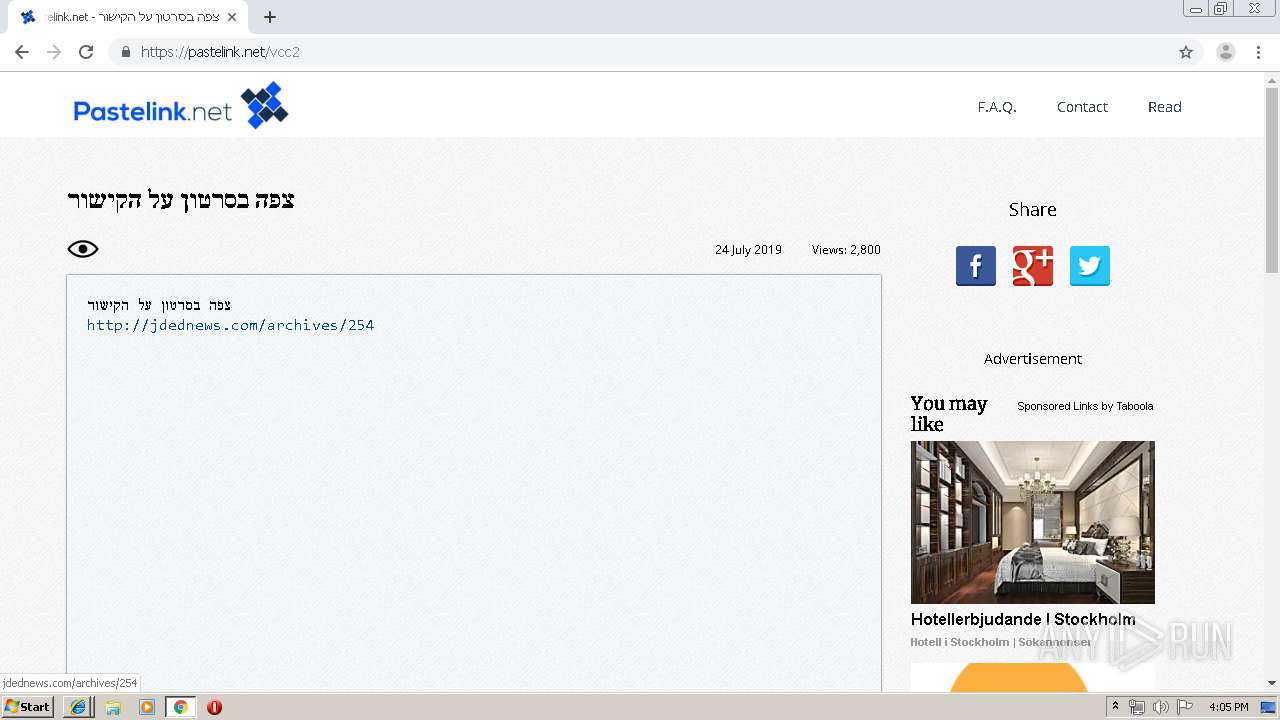
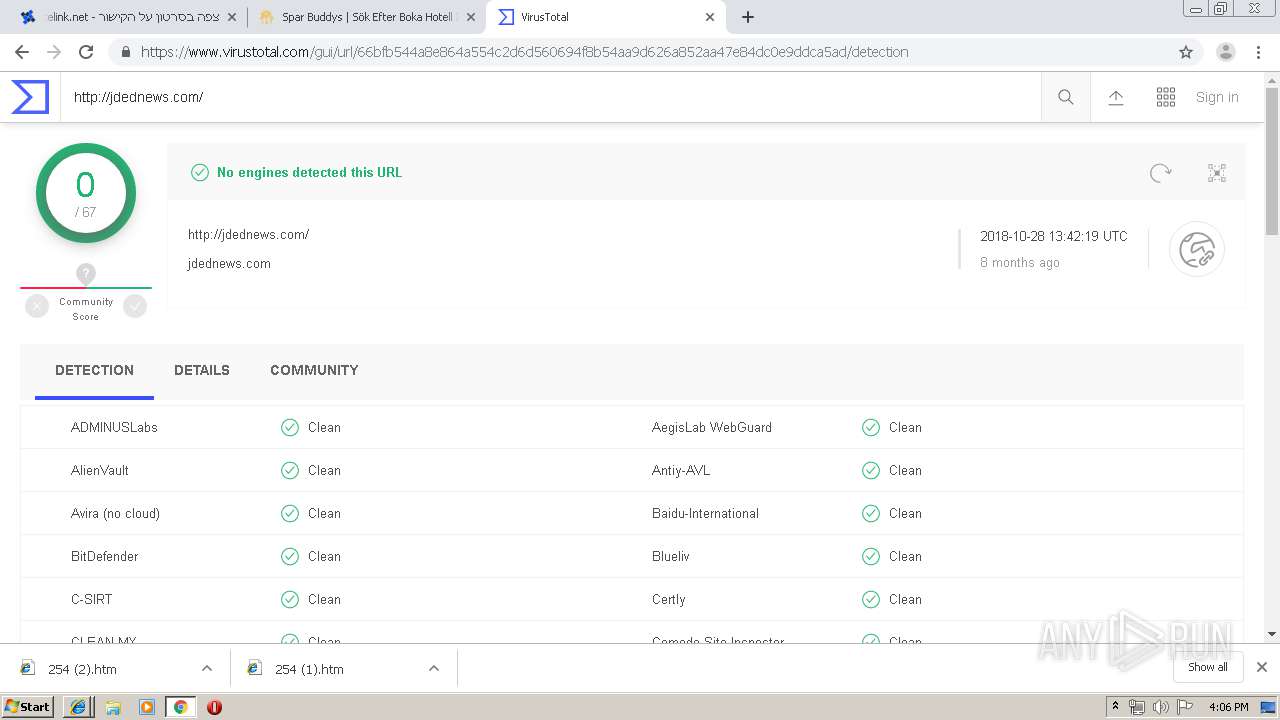
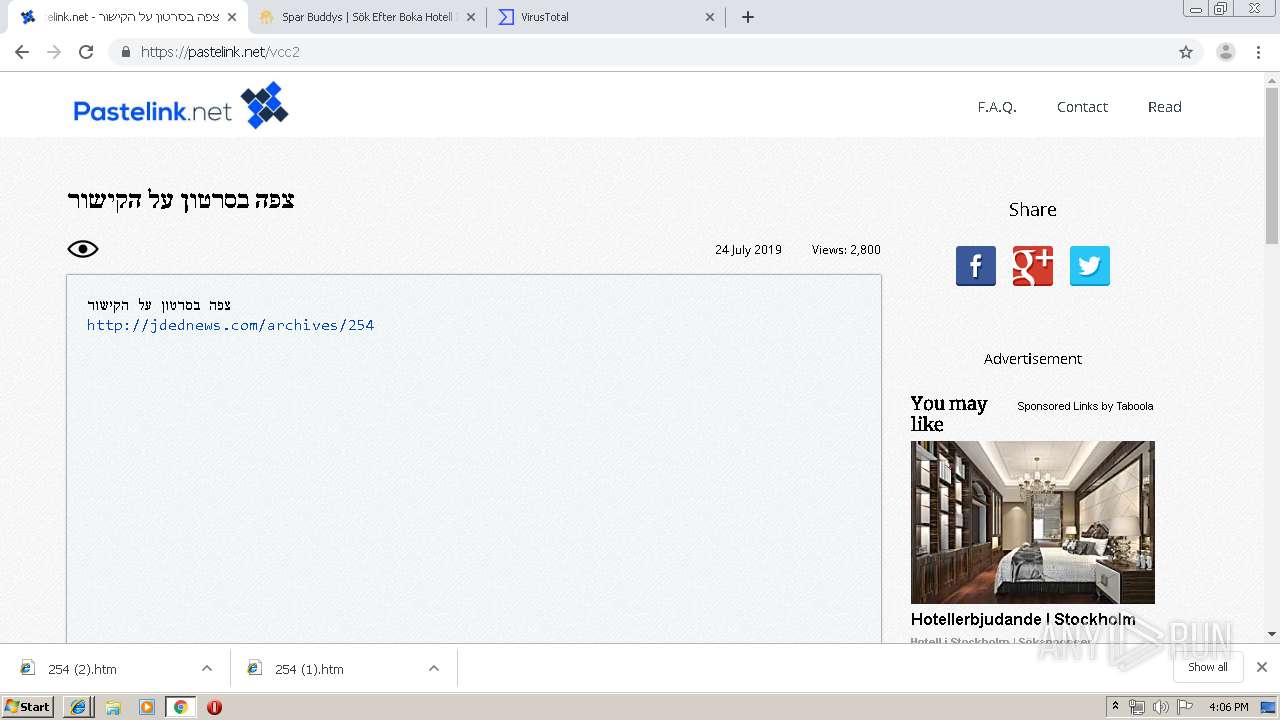
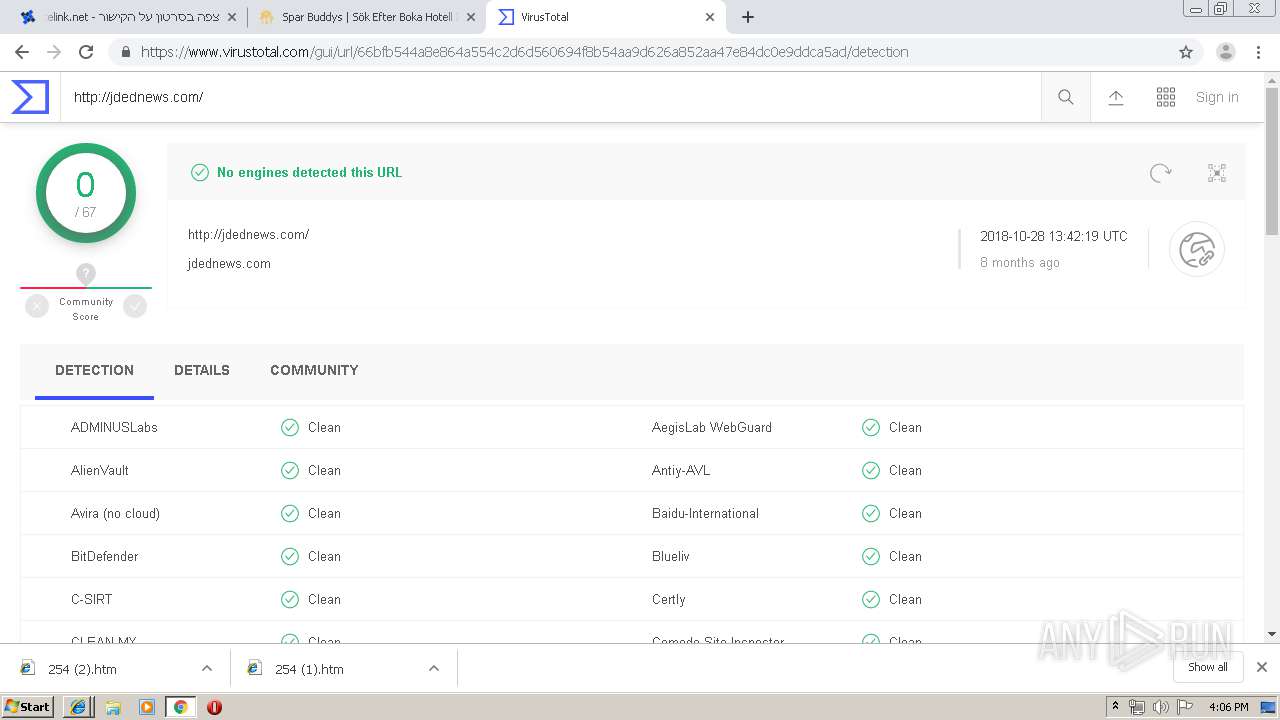
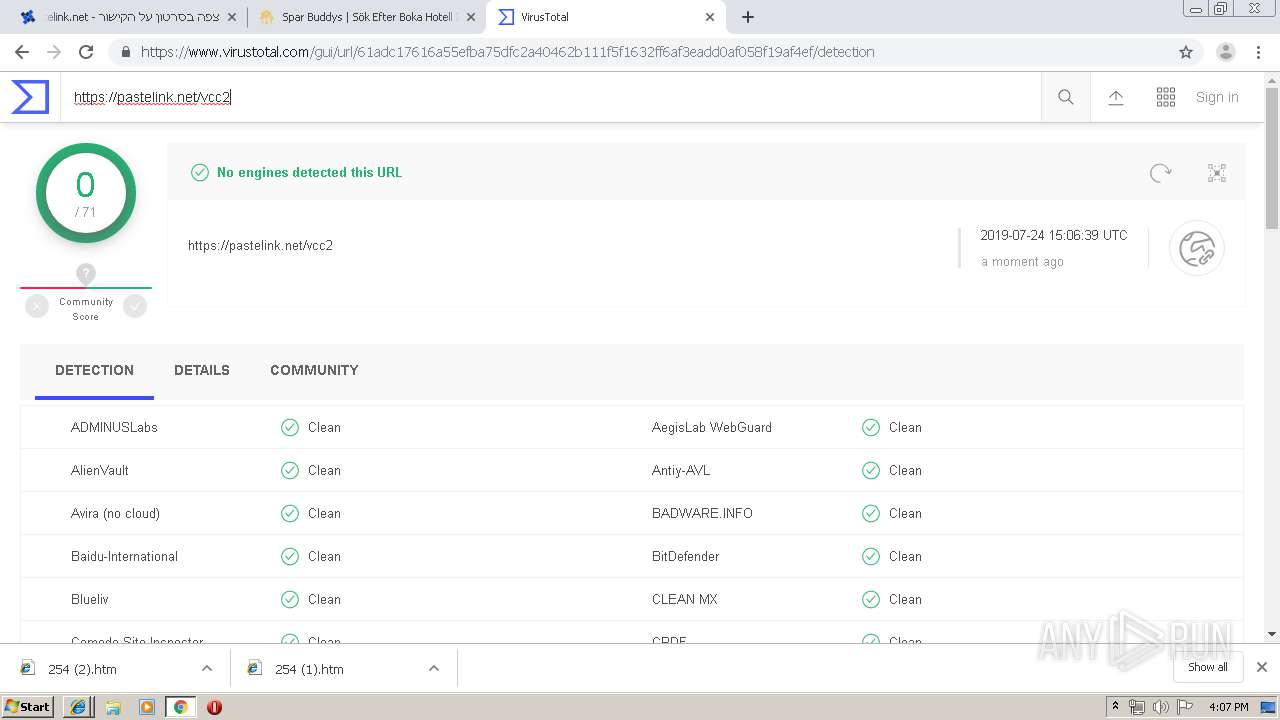
| URL: | https://www.pastelink.net/vcc2 |
| Full analysis: | https://app.any.run/tasks/2966bad4-64f5-429b-a8e1-0d48df5e7443 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2019, 15:02:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7E9B0114627DD70B11D52B5CDF0723B8 |
| SHA1: | 5D4CD6A032D95EFE03EC190E0EEB2C7D91A32E1C |
| SHA256: | 22FD7EA1658BF626A661786AD11FB2C7D470B825BA50B9205AE721D83A6FD317 |
| SSDEEP: | 3:N8DSLvAL0IRX:2OLHU |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3952)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2456)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2708)
Application launched itself
- iexplore.exe (PID: 3900)
- chrome.exe (PID: 2456)
Reads Internet Cache Settings
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2708)
- chrome.exe (PID: 2456)
Changes internet zones settings
- iexplore.exe (PID: 3900)
Creates files in the user directory
- iexplore.exe (PID: 4092)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3952)
- iexplore.exe (PID: 2708)
- chrome.exe (PID: 2456)
Reads settings of System Certificates
- iexplore.exe (PID: 3900)
- iexplore.exe (PID: 2708)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3900)
Changes settings of System certificates
- iexplore.exe (PID: 3900)
- chrome.exe (PID: 2316)
Manual execution by user
- chrome.exe (PID: 2456)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
44
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3900 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.pastelink.net/vcc2" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 4092 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3900 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 3952 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe |
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Version: 26,0,0,131 | ||||
| 2708 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3900 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 2456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6942a9d0,0x6942a9e0,0x6942a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=4060 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 3524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1040,4924589203698984520,6506317022261643096,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9020235493765969830 --mojo-platform-channel-handle=1052 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 75.0.3770.100 | ||||
| 2316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,4924589203698984520,6506317022261643096,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=3383299764273508804 --mojo-platform-channel-handle=1604 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 3760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,4924589203698984520,6506317022261643096,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11325177672163217532 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
Total events
1 854
Read events
1 622
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
338
Text files
345
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3900 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3900 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\8BW8CI0Y\vcc2[1].txt | — | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@pastelink[2].txt | — | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\THOJPES7\css[1].txt | text | |
MD5:75B68541B676BE6FCEE098FFFCA0A015 | SHA256:603EB7B4F1C40F66DE71CA24844F7CA574C5B0A0E5E3A89EF2A8C01807268A9D | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:22D892B9EA0D9EB1381601511E0FC847 | SHA256:77D492B4E14FC7DC1E0FE1F7C1BF14A4B8481500AF7A6E47F6C5C6E99A1C1B24 | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:56639C3A3714F59218B709940815ADCF | SHA256:ED61C1B977F806D4A4967DD41C30DC4765399DE94CA81A83F0A3765D0CE1F3BB | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\8BW8CI0Y\style[1].css | text | |
MD5:4F48A4091FC080AB95C9B21AA3F31BEA | SHA256:0B9F9A60A3473DA8397926580195B9A1B5617881917FA20431E79620A8612B16 | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\8BW8CI0Y\vcc2[1].htm | html | |
MD5:6BC6C6BA43955C3BF5B58B168F491A10 | SHA256:A2CBECDCA7EB18AD668FCED18D4E5A496A82E1553D165256F65C50DFEE1DFF9D | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\THOJPES7\public[1].png | image | |
MD5:4EA2C3FF2DCB52A826AADB9D6AC136F0 | SHA256:04BCD86676A40009FE53606BCE88EDF13537B712F218F9C6057E97C612513092 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
99
TCP/UDP connections
179
DNS requests
114
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
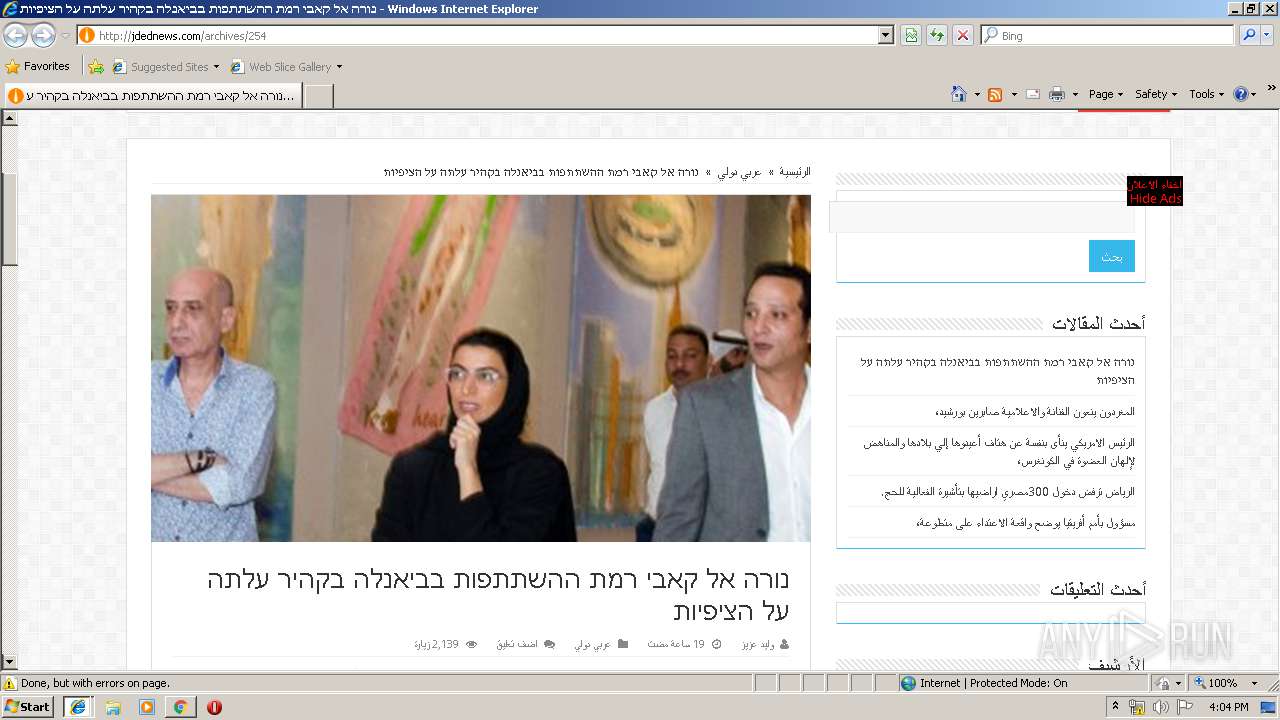
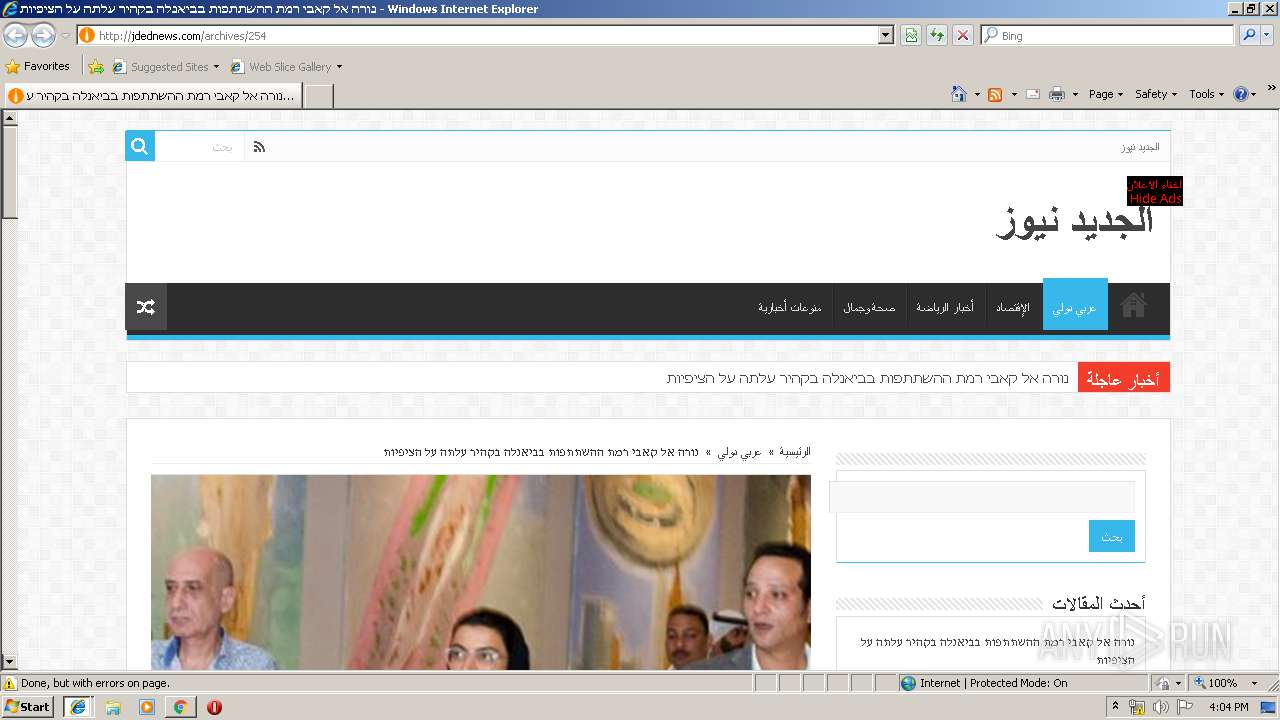
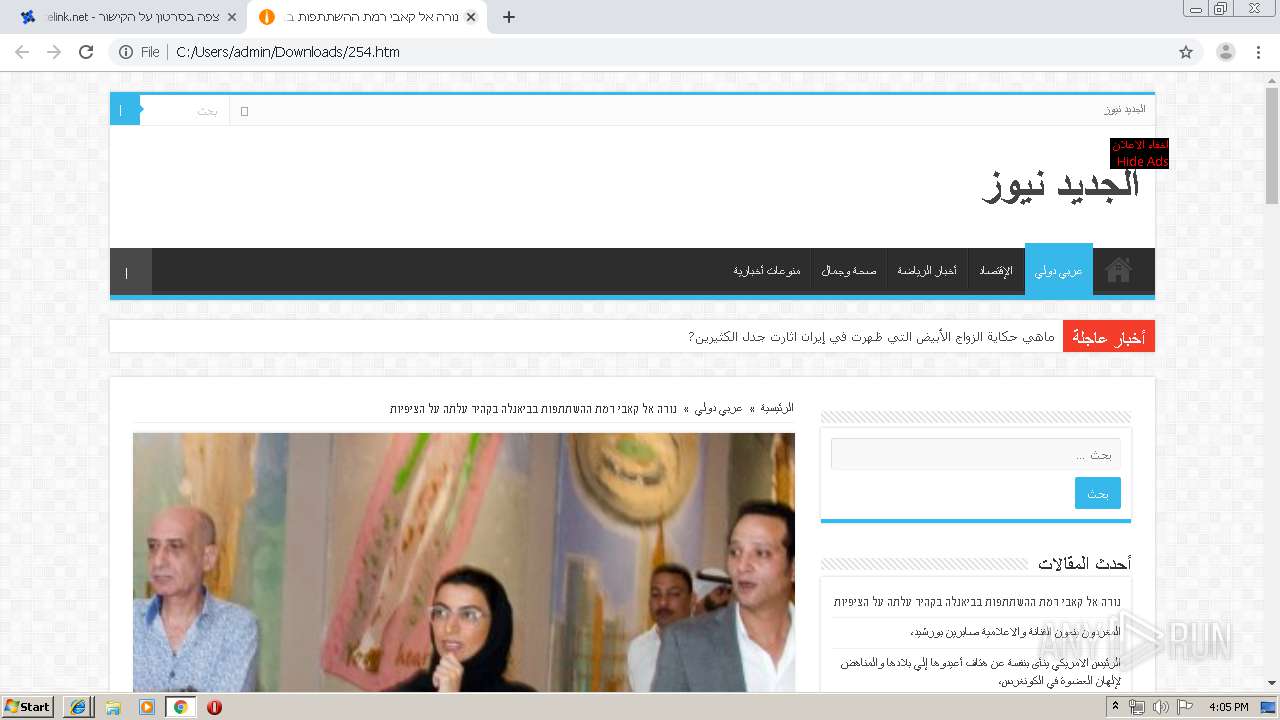
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/archives/254 | FR | html | 14.5 Kb | unknown |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-content/plugins/taqyeem/style.css | FR | text | 1.63 Kb | unknown |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-includes/css/dist/block-library/style-rtl.min.css | FR | text | 4.72 Kb | unknown |
2708 | iexplore.exe | GET | 200 | 172.217.23.162:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 33.4 Kb | whitelisted |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-content/themes/sahifa/style.css | FR | text | 36.8 Kb | unknown |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-content/themes/sahifa/fonts/tiefont/fontello.eot?14434071 | FR | eot | 6.08 Kb | unknown |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-includes/js/jquery/jquery-migrate.min.js | FR | text | 3.92 Kb | unknown |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-content/plugins/taqyeem/js/tie.js | FR | text | 855 b | unknown |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-content/themes/sahifa/css/ilightbox/dark-skin/skin.css | FR | text | 1.30 Kb | unknown |
2708 | iexplore.exe | GET | 200 | 163.172.232.163:80 | http://jdednews.com/wp-content/plugins/taqyeem-buttons/assets/style.css | FR | text | 1.09 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2708 | iexplore.exe | 172.217.23.162:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
4092 | iexplore.exe | 172.217.23.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
4092 | iexplore.exe | 172.217.18.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
4092 | iexplore.exe | 172.217.16.206:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3900 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4092 | iexplore.exe | 151.101.2.2:443 | cdn.taboola.com | Fastly | US | shared |
4092 | iexplore.exe | 178.79.155.87:443 | www.pastelink.net | Linode, LLC | GB | unknown |
4092 | iexplore.exe | 216.58.208.42:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
2708 | iexplore.exe | 172.217.23.138:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2708 | iexplore.exe | 163.172.232.163:80 | jdednews.com | Online S.a.s. | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.pastelink.net |
| unknown |
www.bing.com |
| whitelisted |
pastelink.net |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
cdn.taboola.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
jdednews.com |
| unknown |
www.googletagmanager.com |
| whitelisted |