analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
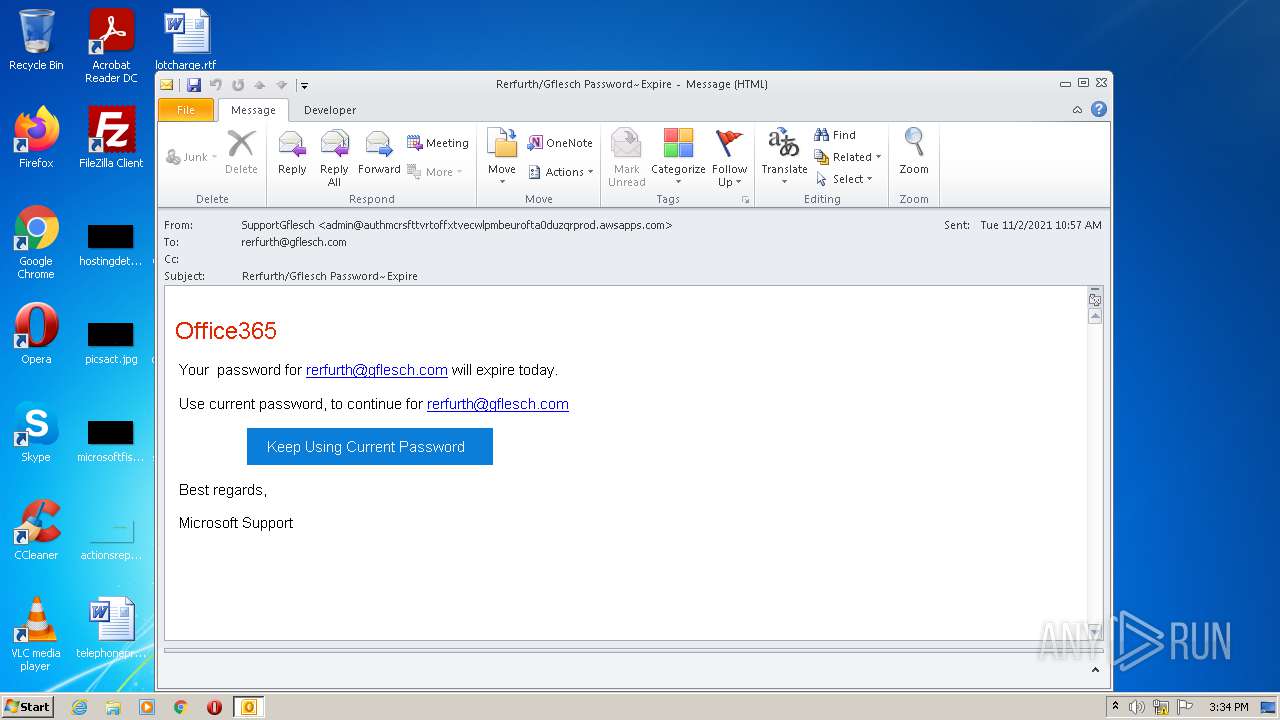
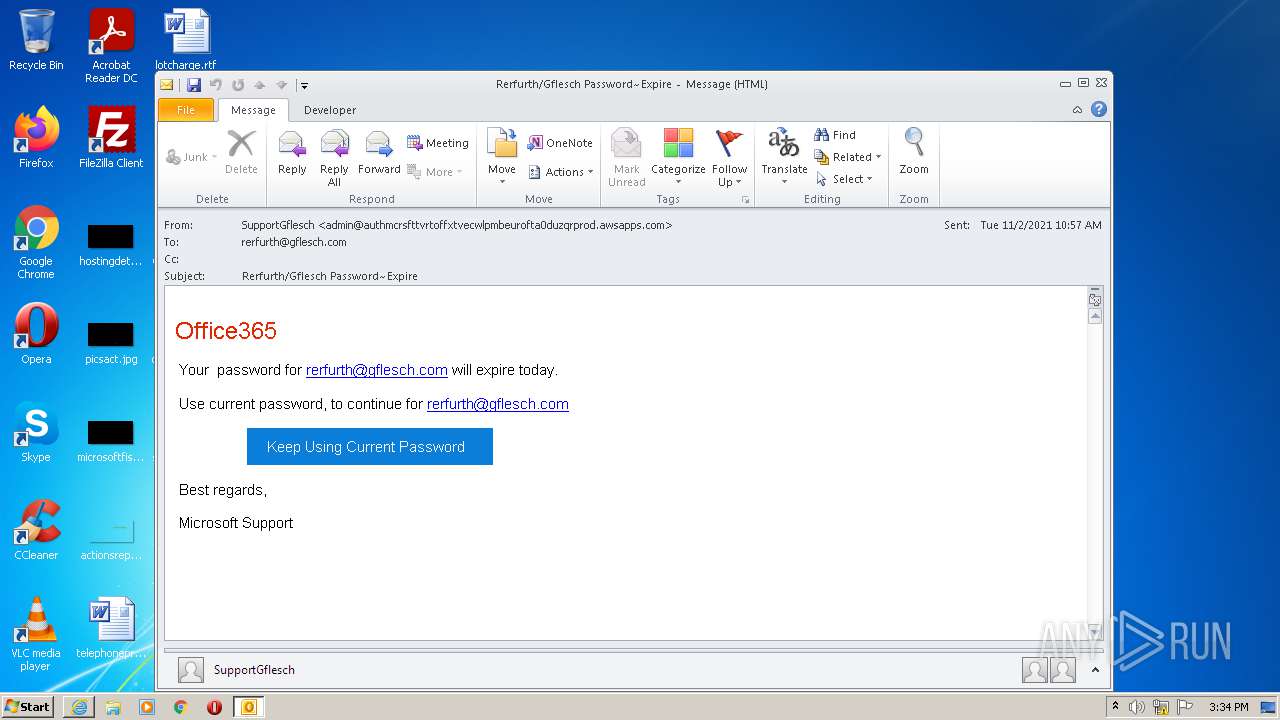
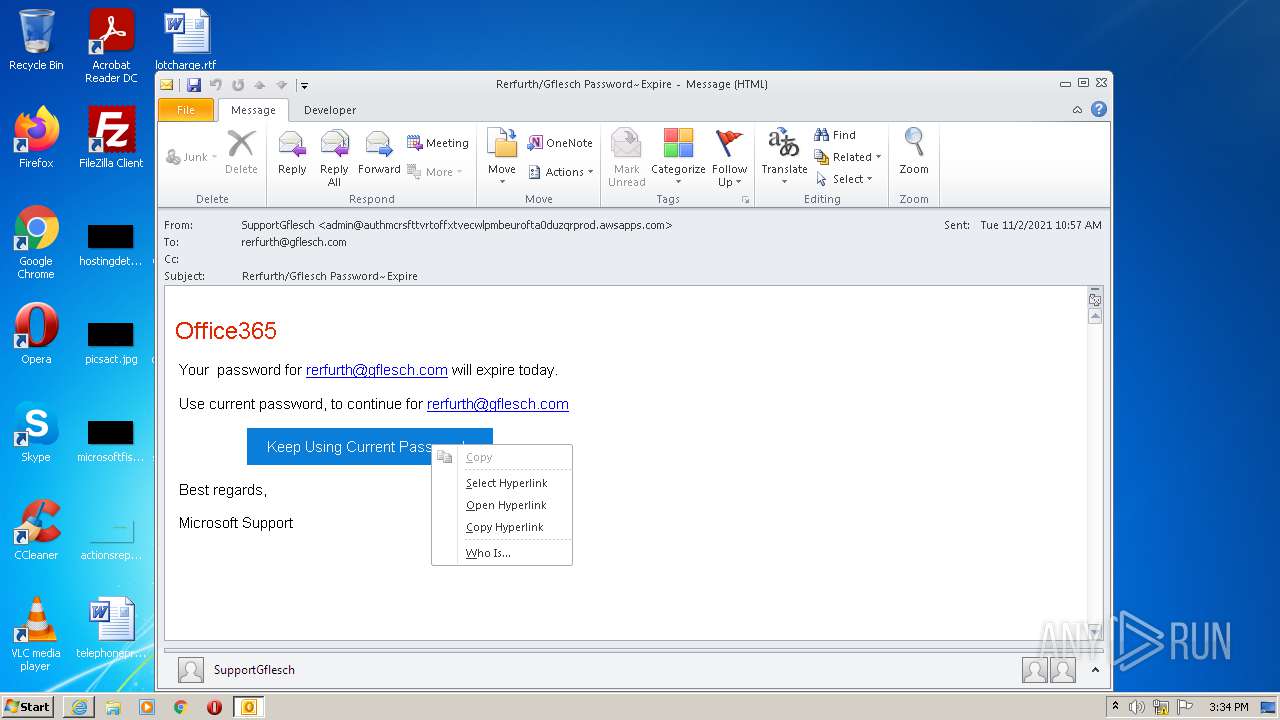
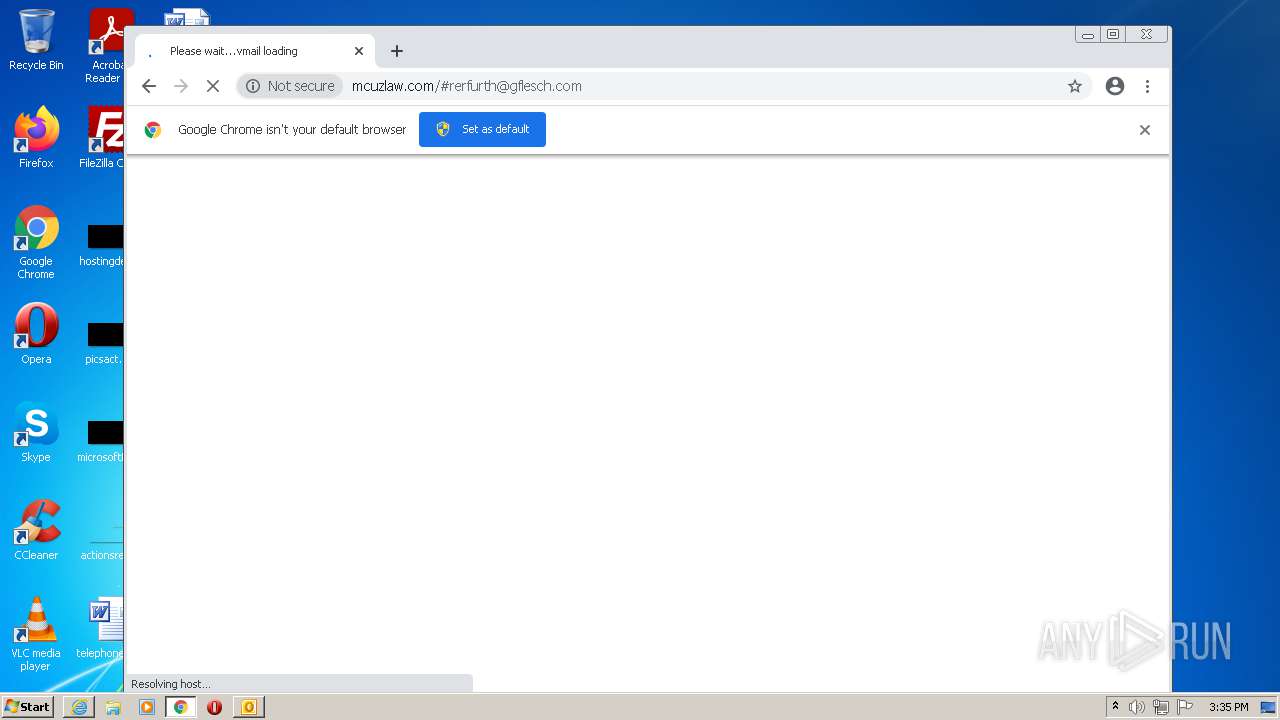
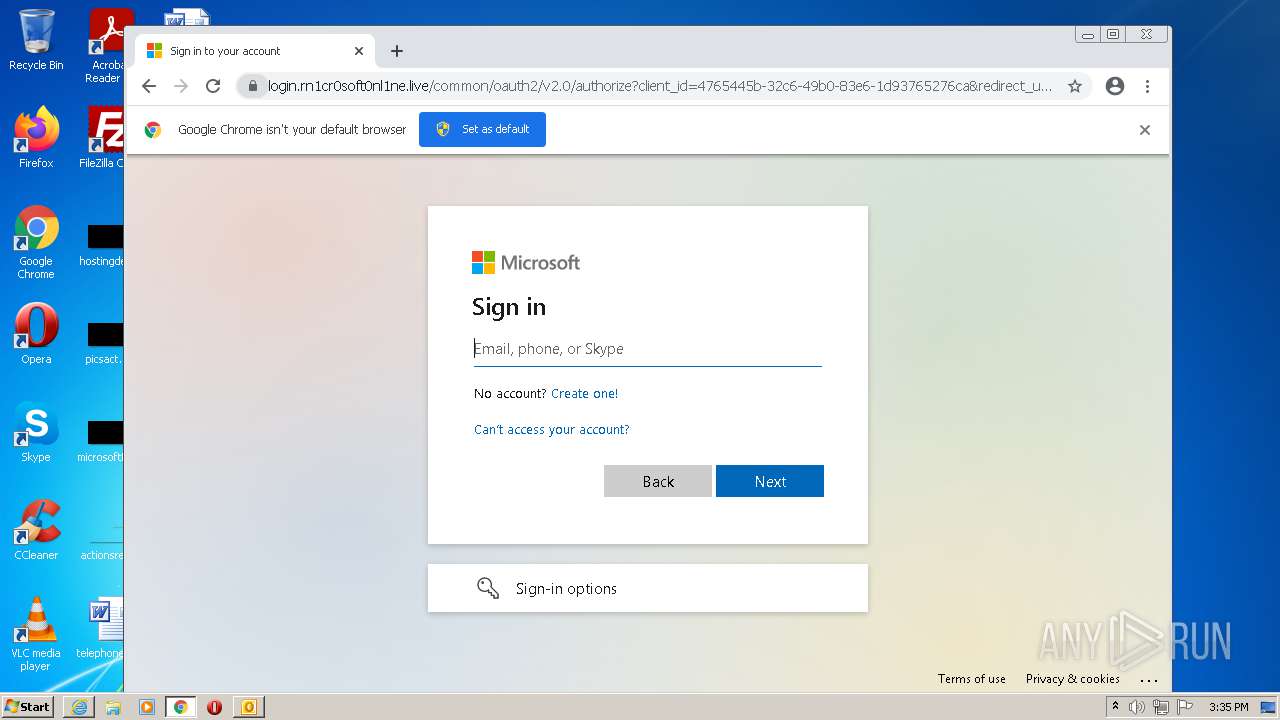
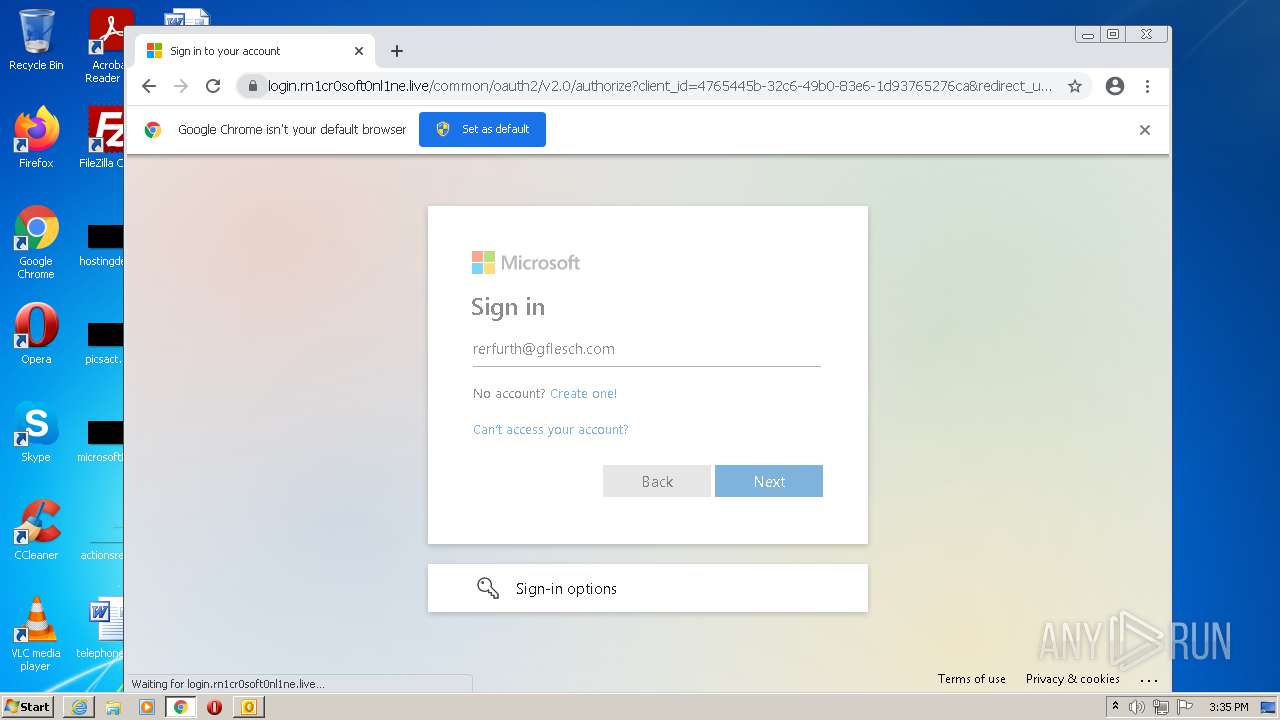
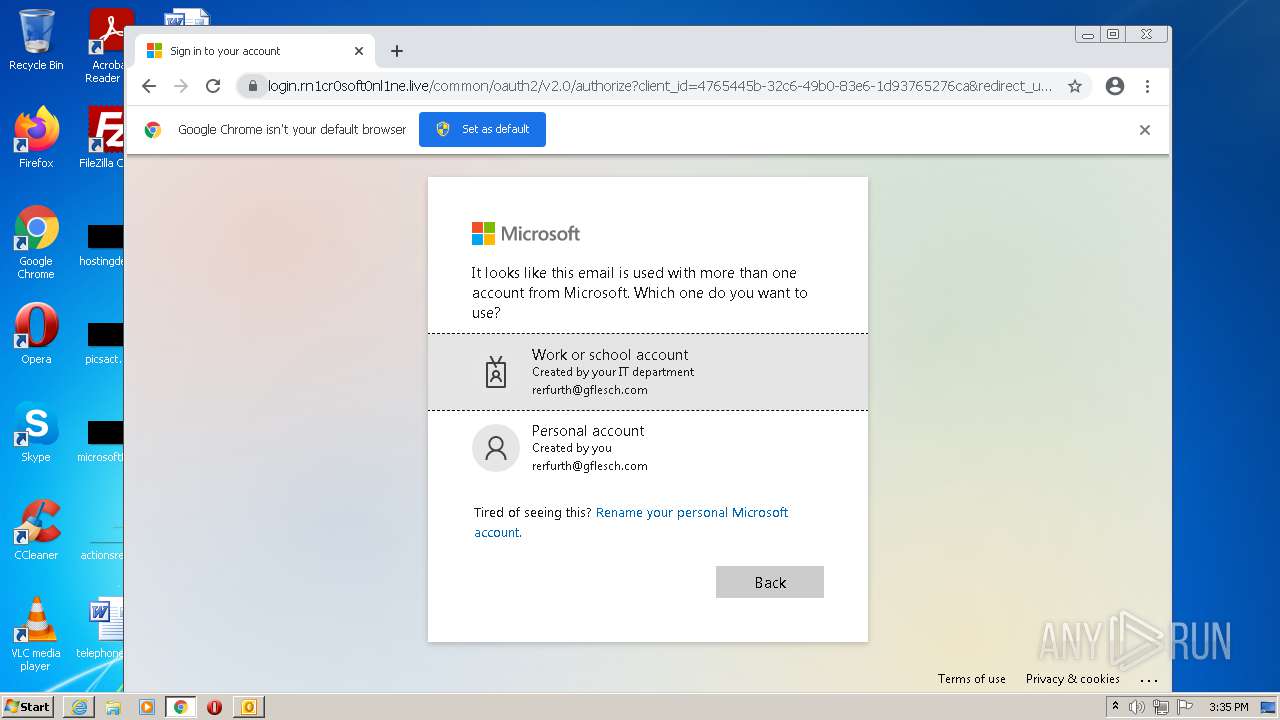
| File name: | 11-2b-RerfurthGflesch Password~Expire.msg |
| Full analysis: | https://app.any.run/tasks/85a97162-2511-4940-b2a1-b3bba597011e |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2021, 15:33:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | A0C17721FC2FCE88CBA167737230D441 |
| SHA1: | 20F488EE3BAD0EDE45CAF35190E60B3598472D5F |
| SHA256: | 7D44BD9091A28600435A652B3F6FF7874AF08156AEDA51B64E73FD50C394AE5C |
| SSDEEP: | 768:4MRWP6pRJer4Gt9ReHOfrFDNhEUWsxlPR/KiDZD1:4MdgzReMR/j1 |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2916)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2916)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3740)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1312)
INFO
Checks supported languages
- OUTLOOK.EXE (PID: 2916)
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 3740)
- chrome.exe (PID: 1312)
- chrome.exe (PID: 2680)
- chrome.exe (PID: 2496)
- chrome.exe (PID: 3008)
- chrome.exe (PID: 3176)
- chrome.exe (PID: 3932)
- chrome.exe (PID: 3884)
- chrome.exe (PID: 2500)
- chrome.exe (PID: 3716)
- chrome.exe (PID: 3788)
- chrome.exe (PID: 1024)
- chrome.exe (PID: 2000)
- chrome.exe (PID: 2000)
- chrome.exe (PID: 2144)
- chrome.exe (PID: 2044)
- chrome.exe (PID: 1604)
- chrome.exe (PID: 3264)
- chrome.exe (PID: 2904)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 3036)
- chrome.exe (PID: 3064)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 3324)
Reads the computer name
- OUTLOOK.EXE (PID: 2916)
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 3740)
- chrome.exe (PID: 1312)
- chrome.exe (PID: 3008)
- chrome.exe (PID: 3176)
- chrome.exe (PID: 3716)
- chrome.exe (PID: 3788)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 3036)
- chrome.exe (PID: 3324)
Searches for installed software
- OUTLOOK.EXE (PID: 2916)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2916)
- iexplore.exe (PID: 3476)
Application launched itself
- iexplore.exe (PID: 3476)
- chrome.exe (PID: 1312)
Changes internet zones settings
- iexplore.exe (PID: 3476)
Reads settings of System Certificates
- iexplore.exe (PID: 3740)
- iexplore.exe (PID: 3476)
- chrome.exe (PID: 3176)
Checks Windows Trust Settings
- iexplore.exe (PID: 3740)
- iexplore.exe (PID: 3476)
Reads internet explorer settings
- iexplore.exe (PID: 3740)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2916)
Reads the hosts file
- chrome.exe (PID: 1312)
- chrome.exe (PID: 3176)
Manual execution by user
- chrome.exe (PID: 1312)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3476)
Changes settings of System certificates
- iexplore.exe (PID: 3476)
Reads the date of Windows installation
- chrome.exe (PID: 3036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
66
Monitored processes
26
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2916 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\11-2b-RerfurthGflesch Password~Expire.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 14.0.6025.1000 Modules
| |||||||||||||||
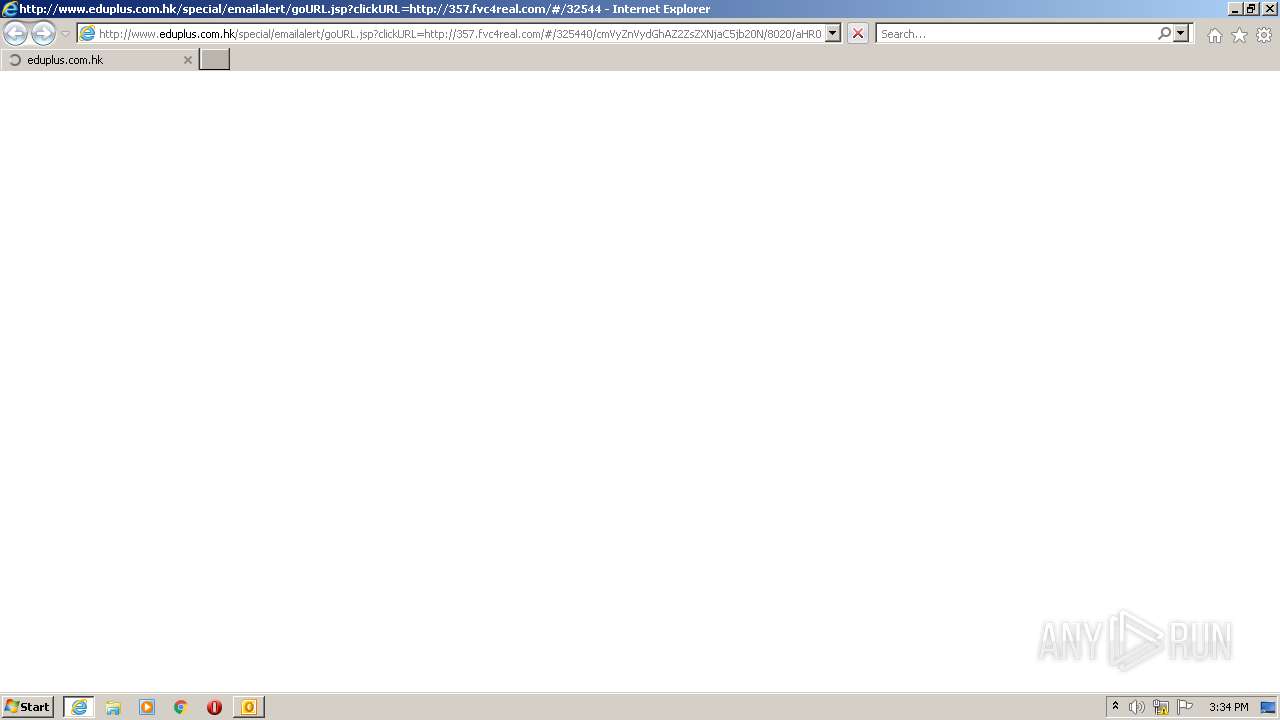
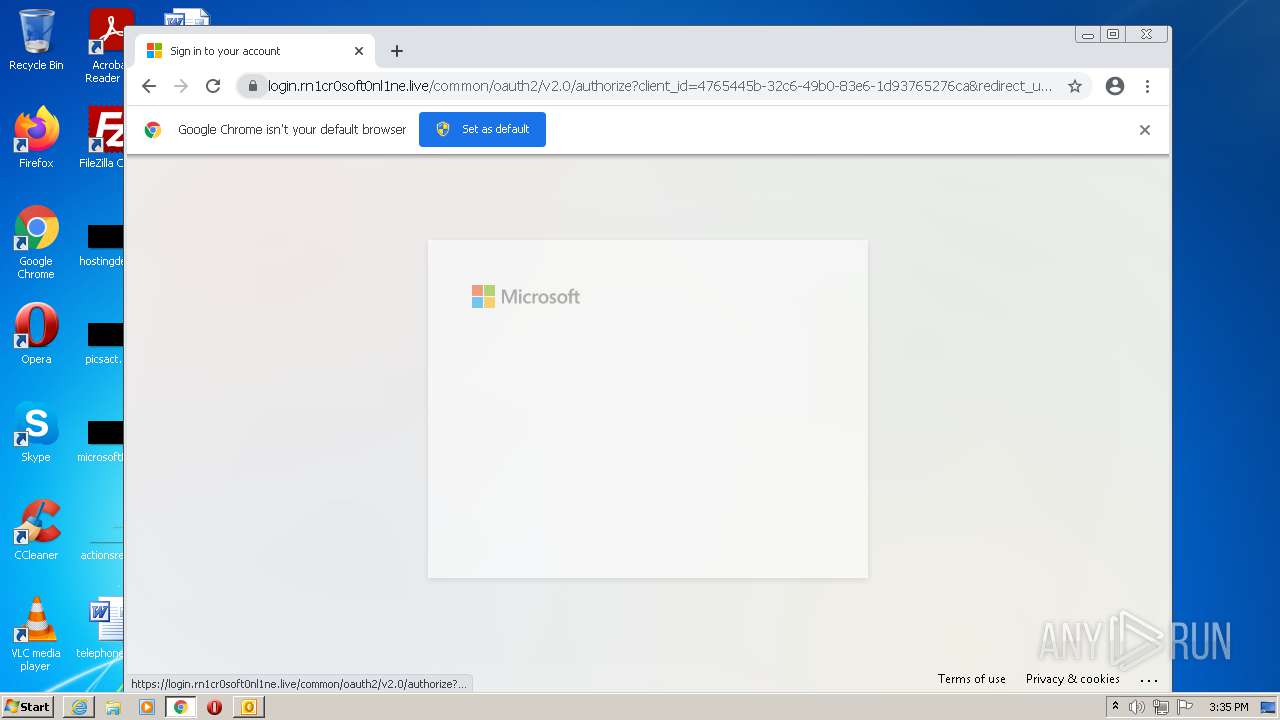
| 3476 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.eduplus.com.hk/special/emailalert/goURL.jsp?clickURL=http://357.fvc4real.com/#/325440/cmVyZnVydGhAZ2ZsZXNjaC5jb20N/8020/aHR0cDovL21jdXpsYXcuY29tLyNyZXJmdXJ0aEBnZmxlc2NoLmNvbQ0=/357 | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3740 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3476 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x5fb2d988,0x5fb2d998,0x5fb2d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 86.0.4240.198 Modules
| |||||||||||||||
| 3008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,16013647568019603333,151874326047221480,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1068 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 3176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1024,16013647568019603333,151874326047221480,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1324 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 86.0.4240.198 Modules
| |||||||||||||||
| 3884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16013647568019603333,151874326047221480,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1928 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 3932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16013647568019603333,151874326047221480,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1936 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16013647568019603333,151874326047221480,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2256 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
33 040
Read events
32 192
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
52
Text files
202
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR730F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:8669CC647D5ECAACC99A5B24A23C9386 | SHA256:C2397BA463214DCDF34C7830D04FE18804093CE26333486BADCC781A085B578C | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:DBBC31CF7AA4069EA6FCE8516F154374 | SHA256:9C18F9B8AACE657216CECAAC75460B171B27EF94B3587C1A875865A3A7CD10E9 | |||
| 3740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:D024DA179EE6ACBF2DA99F469FC733F7 | SHA256:B1C4DDF164181E71BA22E13C84E2AA95C5538330A381946691D4049D08A1D26A | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:7012AF59200A7521FA303CEEA3889B52 | SHA256:BFF2F075DC1CF0E39DF3BB2972D60EC628B2B4C2549CAD199C23ABC146500A99 | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:EC91DBB9F1919037723A45C0F4F94A65 | SHA256:231C2E0F74E82B310A309C7C3433683362E4D8511A566C970247C12FD8B388A5 | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ConversationPrefs_2_53BDE961095CEA448B0A2D9C00B5EA1E.dat | xml | |
MD5:57F30B1BCA811C2FCB81F4C13F6A927B | SHA256:612BAD93621991CB09C347FF01EC600B46617247D5C041311FF459E247D8C2D3 | |||
| 3740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:BEBE0BD67BFD1327C8CF3B82A7E161E2 | SHA256:3F0BD4EB326DEB9475A57BD5C661472D93E165B4462684C04B70B01390574CC5 | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_C244BF17563B9A4EBBAE8CB356C8331E.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
65
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
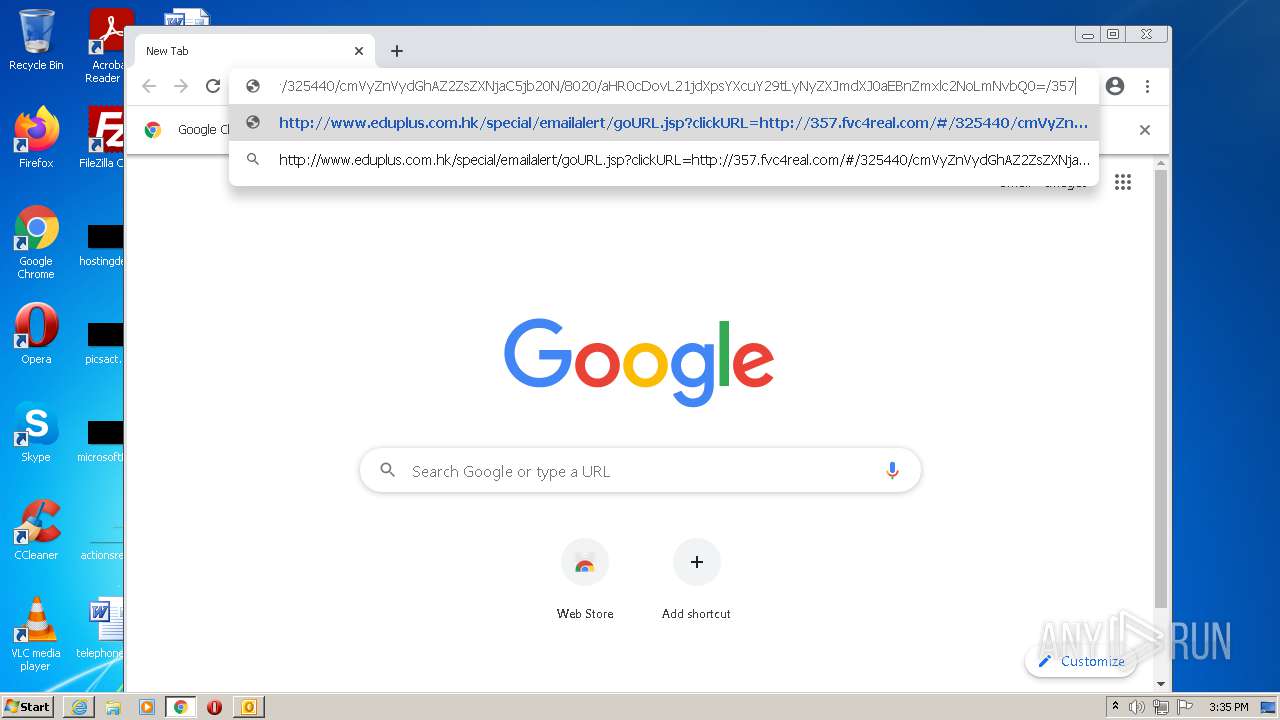
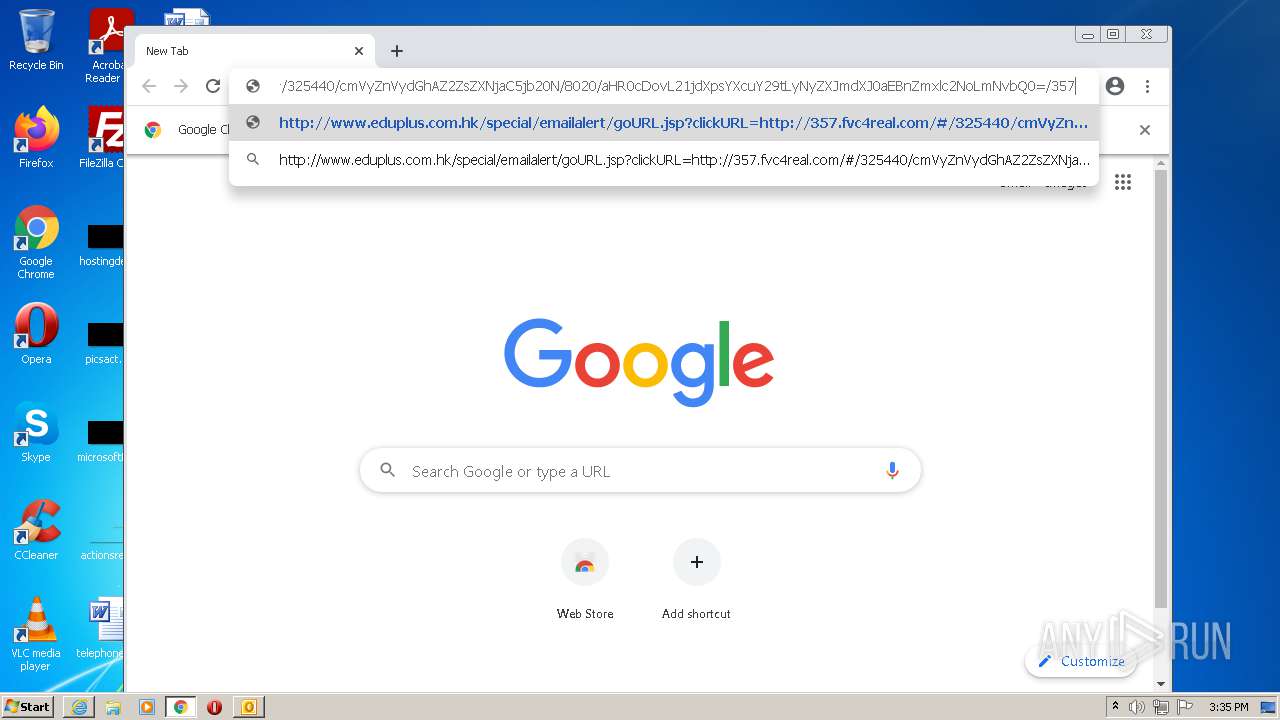
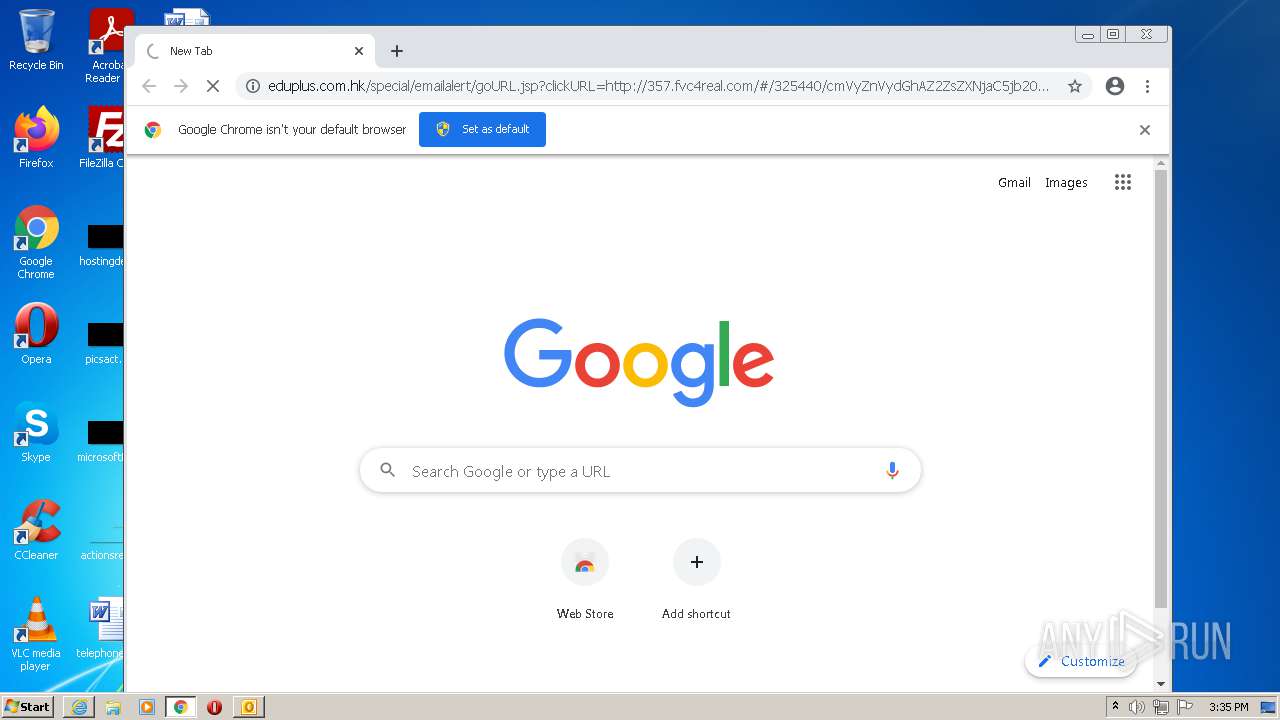
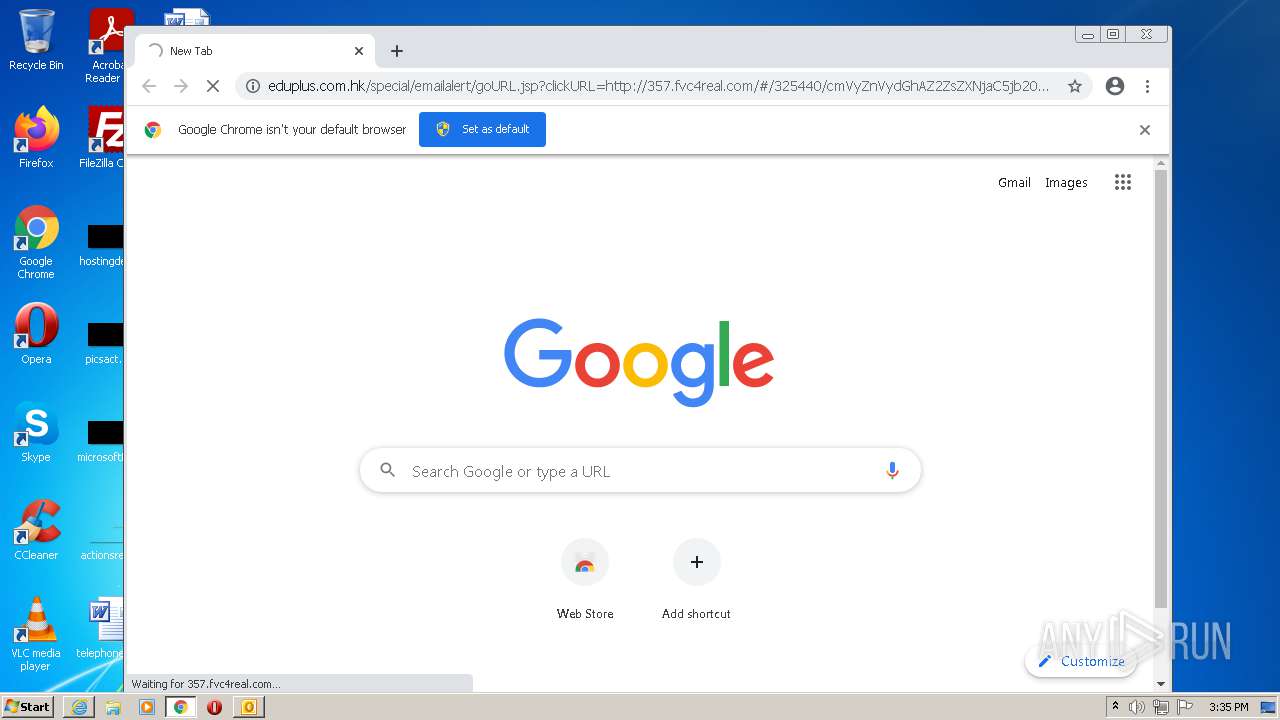
3740 | iexplore.exe | GET | 302 | 203.80.2.138:80 | http://www.eduplus.com.hk/special/emailalert/goURL.jsp?clickURL=http://357.fvc4real.com/ | HK | — | — | unknown |
2916 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3740 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
3476 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3176 | chrome.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bf81662edf5673ca | US | compressed | 59.7 Kb | whitelisted |
3176 | chrome.exe | GET | 302 | 203.80.2.138:80 | http://www.eduplus.com.hk/special/emailalert/goURL.jsp?clickURL=http://357.fvc4real.com/ | HK | — | — | unknown |
3740 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?08d6fb908634aa11 | US | compressed | 4.70 Kb | whitelisted |
3740 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
3740 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCDu0oOI%2BIeHW | US | der | 1.74 Kb | whitelisted |
3476 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2916 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3740 | iexplore.exe | 203.80.2.138:443 | www.eduplus.com.hk | Sing Tao Electronic Daily | HK | unknown |
3476 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3740 | iexplore.exe | 203.80.2.138:80 | www.eduplus.com.hk | Sing Tao Electronic Daily | HK | unknown |
3476 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3740 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3476 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
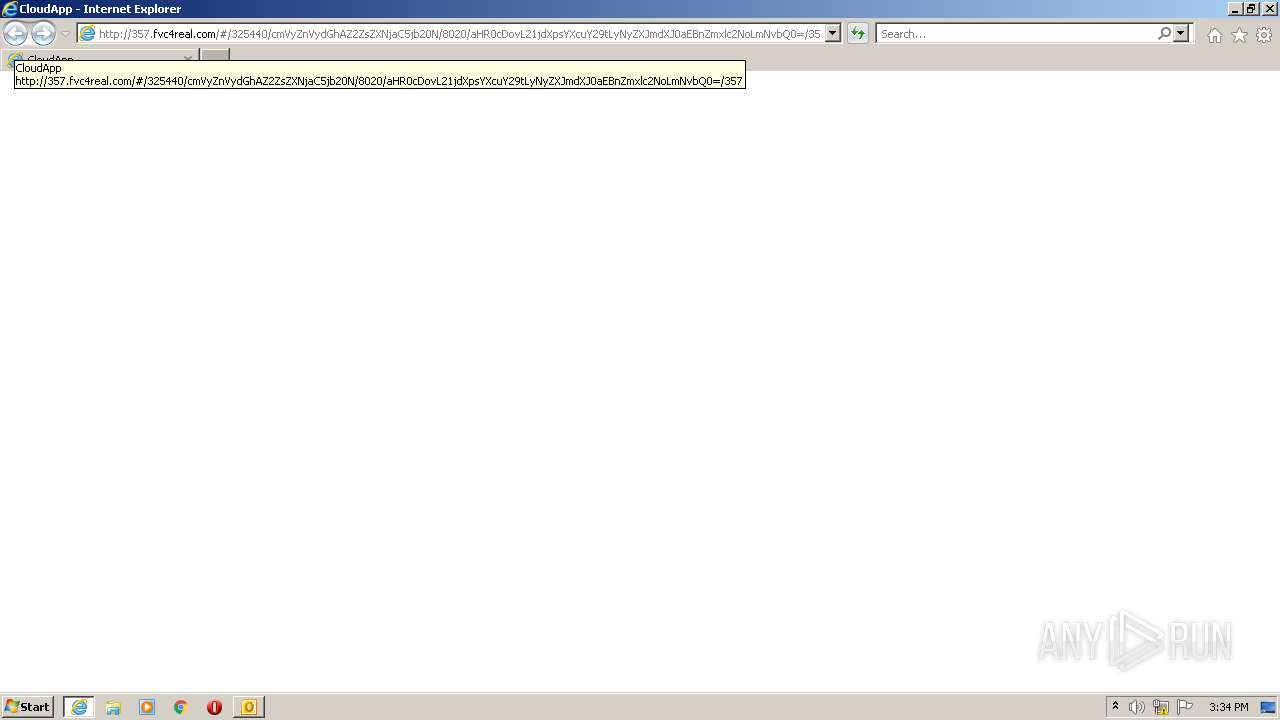
3476 | iexplore.exe | 35.221.179.163:80 | 357.fvc4real.com | — | US | unknown |
3476 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3740 | iexplore.exe | 192.124.249.23:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.eduplus.com.hk |
| unknown |
www.eduplus.hk |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
357.fvc4real.com |
| unknown |
iecvlist.microsoft.com |
| whitelisted |