analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
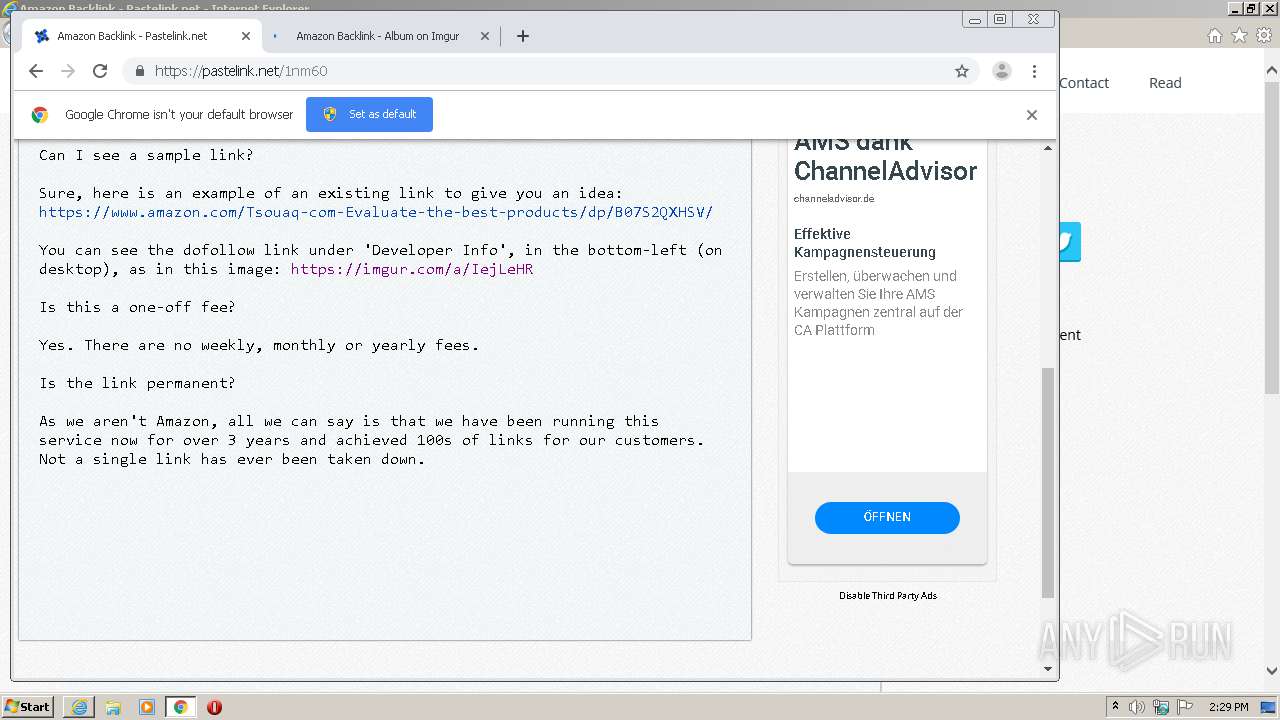
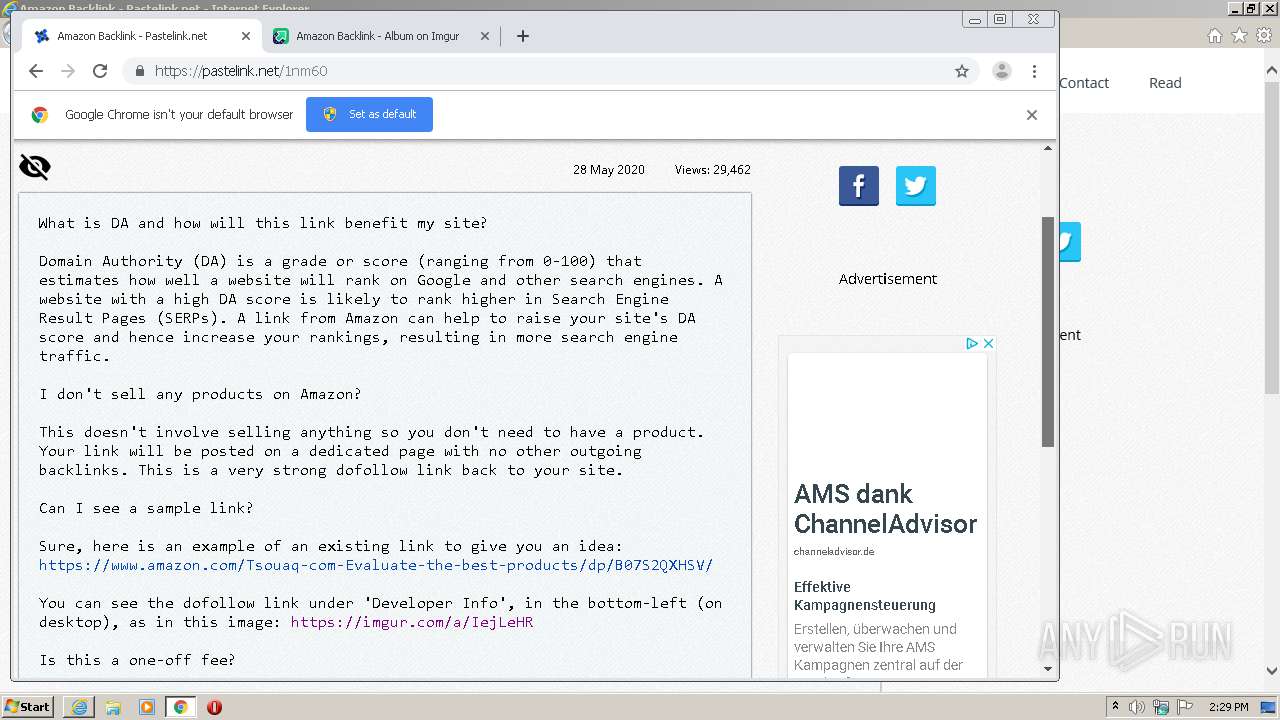
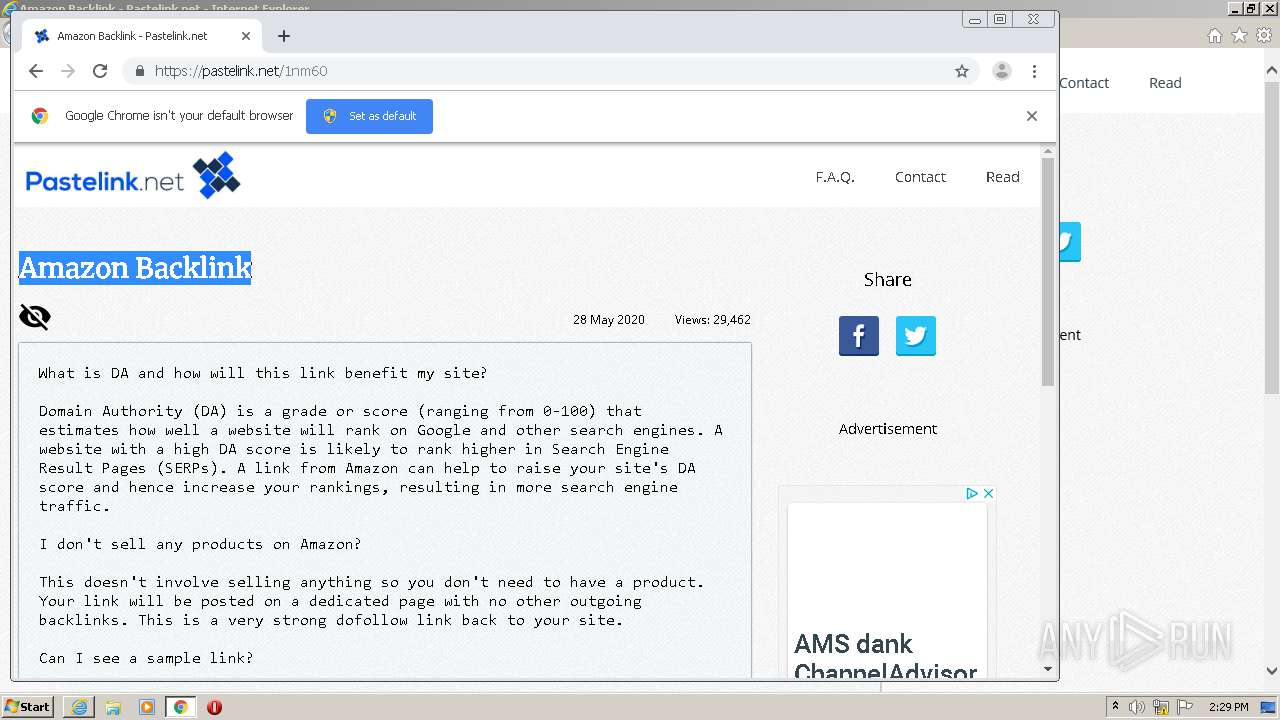
| URL: | https://pastelink.net/1nm60 |
| Full analysis: | https://app.any.run/tasks/3cbc57aa-0fe2-49cc-9d24-c93191c2b7d9 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2020, 13:28:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0D531C61D0EA1771D38507FB4BE26B15 |
| SHA1: | EA11535DDB4286AC06F4767BA7DF76B70C3FCF80 |
| SHA256: | F9BD899CDD1DD0FFD95825C741B338EA434FFFB857355B16799ED9BE19D27FBE |
| SSDEEP: | 3:N8AWsd0za:2AIza |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads settings of System Certificates
- chrome.exe (PID: 584)
- iexplore.exe (PID: 540)
- iexplore.exe (PID: 3660)
Changes internet zones settings
- iexplore.exe (PID: 540)
Application launched itself
- iexplore.exe (PID: 540)
- chrome.exe (PID: 2376)
Creates files in the user directory
- iexplore.exe (PID: 540)
- iexplore.exe (PID: 3660)
Reads the hosts file
- chrome.exe (PID: 2376)
- chrome.exe (PID: 584)
Reads Internet Cache Settings
- iexplore.exe (PID: 3660)
- iexplore.exe (PID: 540)
Manual execution by user
- chrome.exe (PID: 2376)
Reads internet explorer settings
- iexplore.exe (PID: 3660)
Adds / modifies Windows certificates
- iexplore.exe (PID: 540)
Changes settings of System certificates
- iexplore.exe (PID: 540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
64
Monitored processes
27
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 540 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://pastelink.net/1nm60" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 3660 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:540 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 2376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 3828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6e5ea9d0,0x6e5ea9e0,0x6e5ea9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 2640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2556 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1060,6637640584219896694,15068257178216545663,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=4063238342943809852 --mojo-platform-channel-handle=1000 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 75.0.3770.100 | ||||
| 584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1060,6637640584219896694,15068257178216545663,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=4796724708580404265 --mojo-platform-channel-handle=1640 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 75.0.3770.100 | ||||
| 2748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,6637640584219896694,15068257178216545663,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=45768621252905910 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2224 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
| 3796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,6637640584219896694,15068257178216545663,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12543570183565394999 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2528 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 75.0.3770.100 | ||||
| 3272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,6637640584219896694,15068257178216545663,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9360229515065523516 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2492 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
Total events
1 436
Read events
1 213
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
120
Text files
120
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3660 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6F06.tmp | — | |
MD5:— | SHA256:— | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6F07.tmp | — | |
MD5:— | SHA256:— | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\301F5A6CD37A1FEEEB08ABDB97042022 | binary | |
MD5:9C2E1AC8FA407EC2B5785FDA6CBBDB48 | SHA256:FD94681F0BCBF408811FAC3663F9CAF9F51D0DE3B977FCC1FEC2D597AF58E6EA | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\301F5A6CD37A1FEEEB08ABDB97042022 | der | |
MD5:F1F712F19A157885B64261CE86EAAFB1 | SHA256:C4320E7DFE0AB40AA0FED5A6CFCA820603F73C25242DAF610E0169E43751C3E1 | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\hidden[1].png | image | |
MD5:8A6C7A7A0CB95192C3F2A855694866CA | SHA256:6CCF057251B2B50C8ABADF840F6ED4FDE8F061A9C67A794BAE77865C5C7515AD | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:71A103F5033CC423C2518A2EBD514D60 | SHA256:A6B624C99535E4A3A08B245449EA31771EE8EE2A43D1F9E6FC23C02B6A5BD56C | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\script[1].js | text | |
MD5:C2F76905A9EFF753DAEA6BBB0EC6BD99 | SHA256:8F5CAC4B95DB46466763022AB9D251B503C35D388BCDABAB1356C8BE166E4ECA | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | der | |
MD5:BB945DFB3143A6F99A5B69DDF0A57FE6 | SHA256:7811ADEAC77CCE2469E8B3040ED17AD30877977A6997C11F6260522BBC632C6E | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:1C400D233070530C717A810D7F9BC99E | SHA256:58B407B0DDF17FBF78FCB2E2DAD4FABAADA9BD88641F19941480951A200AE4E0 | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\pastelinknet4[1].jpg | image | |
MD5:0C527971219DE523DC22199C0C1D4AA1 | SHA256:262B2A0BAE52D6AFE2F44127D9E9BF02205AD9D02D6BE840F0B8440A45DB0F19 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
125
DNS requests
76
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3660 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3660 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3660 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgNgmpj43LyAoFOuLb6hrtGnZA%3D%3D | unknown | der | 527 b | whitelisted |
540 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3660 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAKhmcGKkEWcAgAAAABzzGw%3D | US | der | 471 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEBB4SLbjrf2YCAAAAABL9g0%3D | US | der | 471 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 950 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDQ1xbKa56n3wIAAAAAcmxg | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3660 | iexplore.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
3660 | iexplore.exe | 172.217.16.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3660 | iexplore.exe | 172.217.18.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3660 | iexplore.exe | 216.58.212.162:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
3660 | iexplore.exe | 178.79.155.87:443 | pastelink.net | Linode, LLC | GB | unknown |
3660 | iexplore.exe | 172.217.22.34:443 | adservice.google.com | Google Inc. | US | whitelisted |
3660 | iexplore.exe | 172.217.23.98:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
540 | iexplore.exe | 178.79.155.87:443 | pastelink.net | Linode, LLC | GB | unknown |
3660 | iexplore.exe | 172.217.18.2:443 | adservice.google.at | Google Inc. | US | whitelisted |
3660 | iexplore.exe | 216.58.212.138:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastelink.net |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |