Back in the early days of iOS extraction, the Zdziarski Method was the goto for acquiring a forensic image of an iPhone. This was quickly adopted by many of the main products and for a short period, all was well with the world of Apple device forensics, until Apple applied hardware encryption.
This has since left analysts with the options of varying levels of logical acquisition and decoding provided by the main vendor’s products, provided you have the passcode/backup password for the device. Obviously, there have been recent advances with offers to LE from main vendors to bypass passcodes and the new Grayshift black boxes on offer.
A large portion of the information which we as analysts want to parse and analyse does tend to sit in many of the logical areas accessible by these tools and some of the extraction methods are essentially just iTunes backups.
So what if we could extract iTunes backups using some open source tools using just our Mac or Linux box?
Enter Homebrew and the libimobiledevice tools.

Homebrew is a package manager for macOS which allows you to run Linux tools natively on the mac.
Installation
Installing Homebrew is pretty trivial and instructions for this can be seen on the Homebrew site: https://brew.sh/
Once Homebrew is installed, we need to then add the libimobiledevice cask.
This can be done by running the command to install:
brew install libimobiledevice
Extraction
Running the ideviceinfo command initially shows the following output:
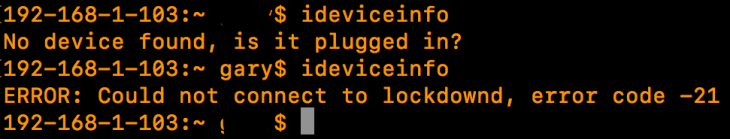
We will be required by iTunes to unlock the iPhone with the users passcode and then selecting trust on the handset, and entering the passcode a second time.
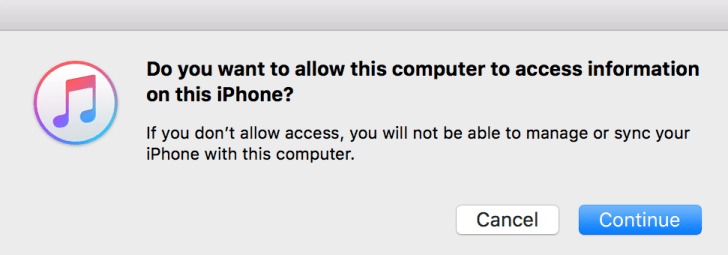

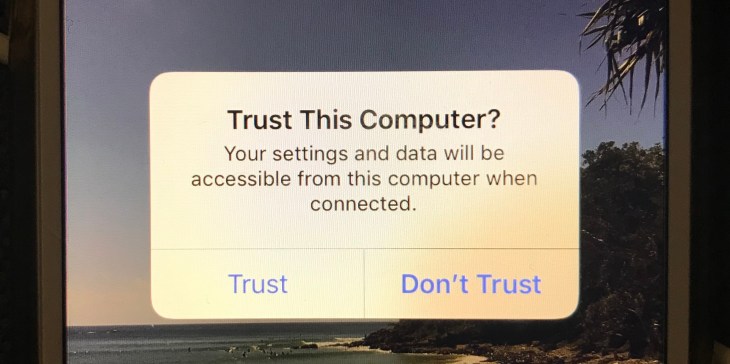
Once we have trust between the iPhone and Computer we can then continue to query the device.
With the ideviceinfo tool, we can establish some basic information about the device.
BluetoothAddress: 8x:xe:x2:xa:1x:xa
EthernetAddress: xc:8x:x2:xa:x6:ax
FirmwareVersion: iBoot-4076.50.126
IntegratedCircuitCardIdentity: 8961xx46xxxxxxxxx9
InternationalMobileEquipmentIdentity: 358xxxxxxxx66
InternationalMobileSubscriberIdentity: 50502xxxxxxxx6
MobileEquipmentIdentifier: 35xx71xx553xx6
PhoneNumber: +61 000 000 000
ProductName: iPhone OS
ProductType: iPhone8,1
ProductVersion: 11.3.1
TimeZone: Australia/Sydney
WiFiAddress: 8c:8e:xx:4a:16:xx
For analysts who have worked in units or departments where they have the authority to perform subscriber checks, you will spot some important information here which can be used and go a long way to attribution. You will also notice that there is information here which can be used to identify the device on wireless networks.
I will generally send the output from this command to a text file to accompany the backup. As you can see there are a number of options including one to dump a list of files to CSV, unpack the backup and also to disable backup encryption (you will need to feed it the backup password to do this).

We can perform an iTunes backup from Terminal using the following command:
idevicebackup2 backup /pathtobackup
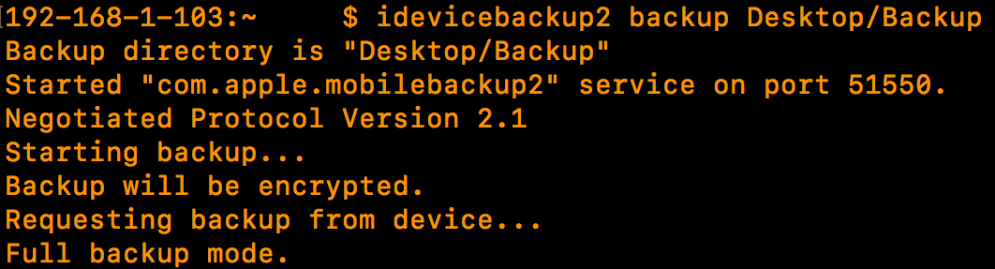

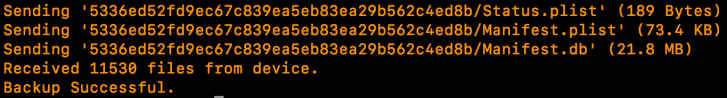
Once it completes, we are free to start interrogating our backup using other tools whether that be a product from one of the main vendors, other open source tools or some of the cheaper products which fall somewhere in-between. Please note that the iTunes backup password will be required to decode the contents of the backup.
Reference:
http://www.libimobiledevice.org/
https://www.zdziarski.com/blog/
https://graykey.grayshift.com/
