Hackers exploit the PHP Git repository adding backdoor to PHP’s source code
9 minutes reading
According to the latest online sources, HostArmada can confirm that the official PHP git repository, at http://git.php.net/, was the target of two malicious attacks made on 2021-03-28. Hackers pushed the two malicious exploits to the php-src repo from Rasmus Lerdorf and Nikita Popov’s names. It is unknown how exactly this happened, but everything points towards hackers compromising the git.php.net server (rather than compromising any individual git account).
HostArmada continues to be a reliable source of news. After our latest blog post about cybersecurity, we continue the trend of reporting the major news that our clients and other interested parties should keep an eye out for. Please keep reading to find out more about this incident as it develops!
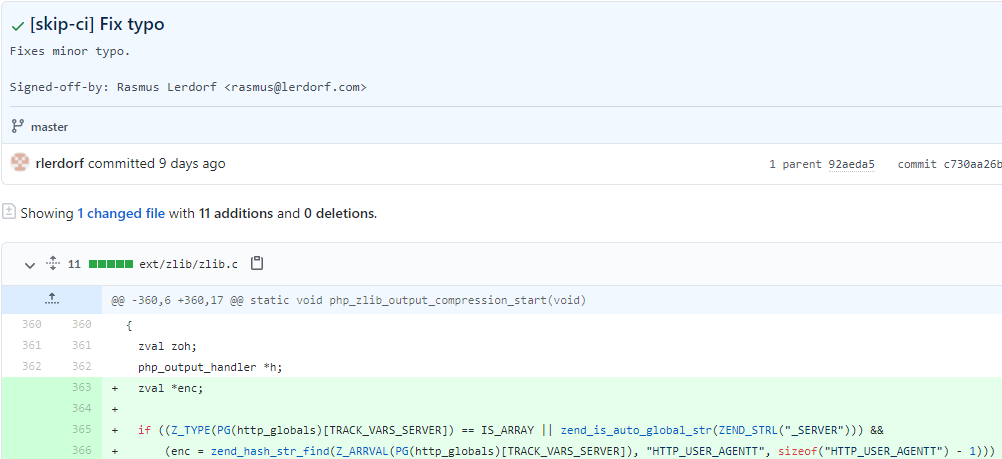
Here are the two referenced commits that we are talking about in this blog post:

What did the hackers do?

Everything points towards a compromise of the git.php.net server. Hackers pushed the backdoored code on the server under the guise of a very minor and inconspicuous edit. The malicious attackers pushed the two commits to the php-src repo for the popular scripting language. This backdoor would have allowed them to perform remote code execution (RCE), PHP maintainers revealed in an official statement. These unknown chaos agents would have used the backdoor for the remote takeover of any website that uses PHP. Maintainers are now reviewing the repositories for any signs of further compromise.
The security incident can be described as a supply-chain attack. Threat actors will target an open-source project, library, or another component that is relied upon by a large user base. By compromising one core target, it may be possible for malicious code to trickle down to a wide-reaching number of systems.
A recent example is the SolarWinds fiasco, discussed in our previous blog post, in which the vendor was breached, and hackers planted a malicious update for its Orion software. Once malicious users deployed this malware, tens of thousands of organizations were compromised, including Microsoft, FireEye, and Mimecast.
An investigation is still underway with no confirmed reports pointing to the identity of the attacker.
The malicious code includes reference to ‘Zerodium,’ a US company known for buying zero-day exploits. The company has so far denied involvement. In a tweet Zerodium CEO said:
“Cheers to the troll who put ‘Zerodium’ in today’s PHP git compromised commits. Obviously, we have nothing to do with this. Likely, the researcher(s) who found this bug/exploit tried to sell it to many entities, but none wanted to buy this crap, so they burned it for fun.”
Zerodium CEO Chaouki Bekrar
Repercussions of the attack
While preliminary investigations are still underway, PHP maintainers have decided that maintaining their own git infrastructure is an unnecessary security risk at this time. In the interest of cybersecurity and to prevent other hackers from interfering, they will discontinue the git.php.net server. As of right now and indefinitely. Instead, the repositories on GitHub, which were previously only mirrors, will become canonical. This means that in the future, they should push changes directly to GitHub rather than to git.php.net.
Previously the write access to repositories handles through their home-grown karma system. You will now need to be part of the PHP organization on GitHub. If you are not part of the organization yet or don’t have access to a repository you should have access to, contact Nikita Popov at [email protected] with your php.net and GitHub account names, as well as the permissions you’re currently missing. Membership in the organization has to have 2FA turned on. This change also means that it is now possible to merge pull requests directly from the GitHub web interface.
Have the hackers left Github users unsafe?
Hackers may indeed have exploited the PHP repository itself. However, PHP maintainers found the backdoor left by the attacker(s) early. This was way before its malicious code could have reached the latest PHP release. This means that no released versions of PHP included this backdoor. This has prevented what could have been a major disaster for the global online community. According to a Web Technology Surveys study, PHP is thought to underpin almost 80% of all websites. This includes all WordPress sites, which are built on PHP.
The PHP team is currently reviewing the repositories to ensure that no other modifications were made by the attacker(s), but nothing has been found up to now. HostArmada will continue to monitor the situation further to provide you with updates as it develops further. We are quite eager to hear the results of the investigation!
In the wake of the Microsoft Exchange Github Scandal
This wasn’t the only cybersecurity alert that has happened for Github in the recent past. After security researcher Nguyen Jang posted a proof-of-concept exploit on GitHub that abuses a Microsoft Exchange vulnerability revealed earlier, GitHub, which is Microsoft-owned, removed the code to the alarm of security researchers worldwide.
The PoC code, something short of an actual functioning exploit, consisted of a 169-line Python file. It took advantage of CVE-2021-26855, a Microsoft Exchange Server flaw that allows an attacker to bypass authentication and act with administrative privileges. The bug, referred to as ProxyLogon, was one of four Microsoft Exchange zero-days that Microsoft patched in an out-of-band release on March 3, 2021. It’s part of the “Hafnium” attack that prompted a US government warning last week, which we’ve also discussed in our previous blog post.
Jang posted a write-up of his work, in Vietnamese, with a link to the code on GitHub. And a few hours later, the link to the code on GitHub no longer functioned.
It is safe to say that this bodes some concern over Microsoft’s ability to handle cybersecurity threats and its ability to hold wholesome interactions with cybersecurity researchers and experts. We’ll have to monitor how the giant techno-corp will react and adapt to this uncertain and dangerous climate. We wish them luck and success in this endeavor!
Closing Remarks
Expect us to be following the trends in cybersecurity in future blog posts as well. There is a lot to cover and currently happening across the world. The timing isn’t great either, given the rest of the issues the denizens of Earth are currently experiencing as a global society and the Covid-19 pandemic. The last thing we need is an unstable world wide web filled with threat actors looking to exploit big corporations and regular internet users in criminal and malicious ways. Unfortunately, that is what the current climate is showing us. Regardless this is an opportunity for companies such as HostArmada to raise awareness about these issues and be part of our global efforts to innovate and adapt to these new challenges.
Furthermore, we here at HostArmada, want to assure you that we have not been impacted by these cybersecurity threats as of now and are only reporting them to make sure our clients are well-informed about the state of the digital world.
If you have further questions, suggestions, or concerns, you can always reach us. HostArmada remains ready to be deployed 24/7!