There are numerous information sources available for cyber threat intelligence (CTI) operations, but they are divided into three major categories: Surface Web intelligence , Dark Web intelligence and Deep web intelligence. The internet is what most users experience every day through their email client and web browser, however there are a number of expansive services that function in the background, and the “web” is only one aspect of it.
Also Read: IOC vs IOA: Indicators of Threat Intelligence
There are numerous layers behind that web browser that the common user may only see tangentially or never see.The web is generally divided into three sections: the Surface Web, the Dark Web, and the Deep Web.We can use the comparison of an iceberg to illustrate the distinction between the Surface Web , Dark Web and Deep Web.
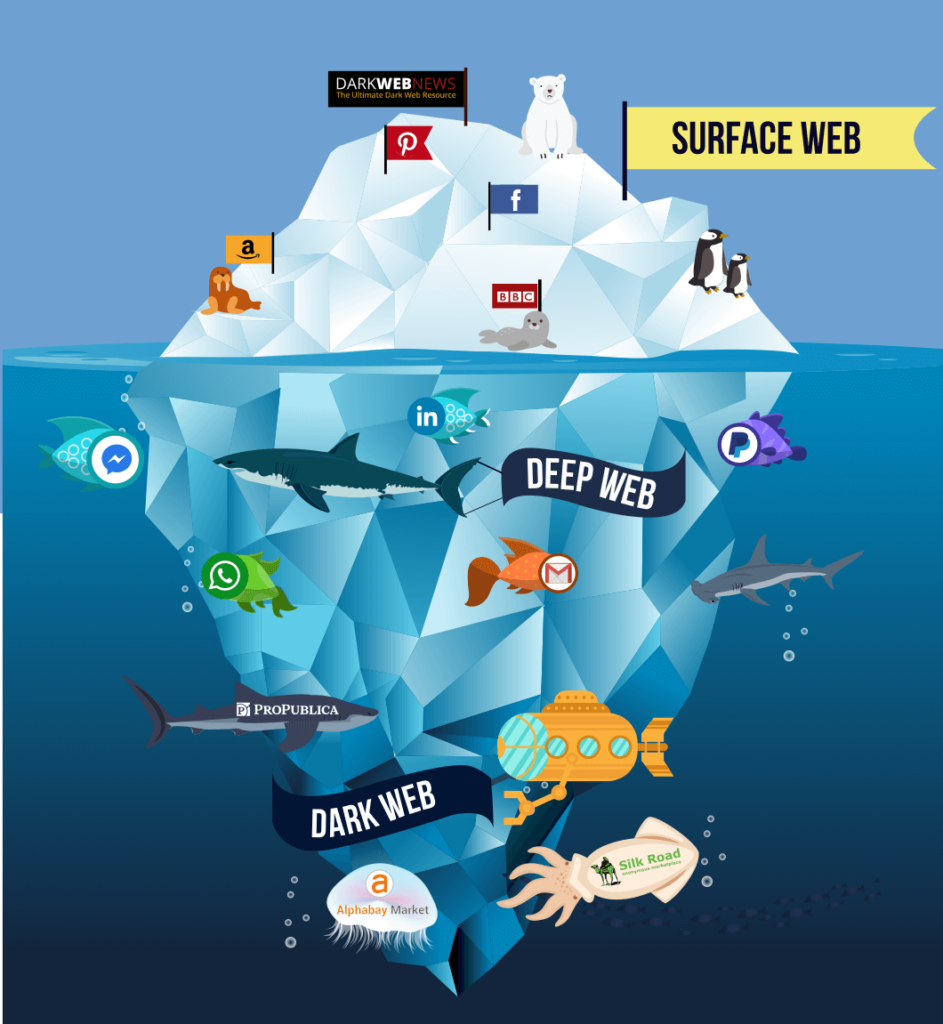
The Surface Web
Users browse the Surface Web as part of their routine daily activities.It may be found using common search engines and can be visited using common web browsers like Mozilla Firefox, Microsoft’s Internet Explorer or Edge, and Google Chrome that don’t need any additional configuration.
Example Use cases:
- Seo poisoning in which adversaries leverage search engines to retrieve their malicious website top of the search engine for the specific keyword and infect the victims. Although getting ranked for the top keywords is difficult for new websites, still this can be achieved by enrolling as an advertiser with famous search engines ad services such as Google adsense , Yahoo & more Ad providers. Top advertisement companies should make sure to validate both advertisers and publishers websites URL and check for malware codes in the source code.
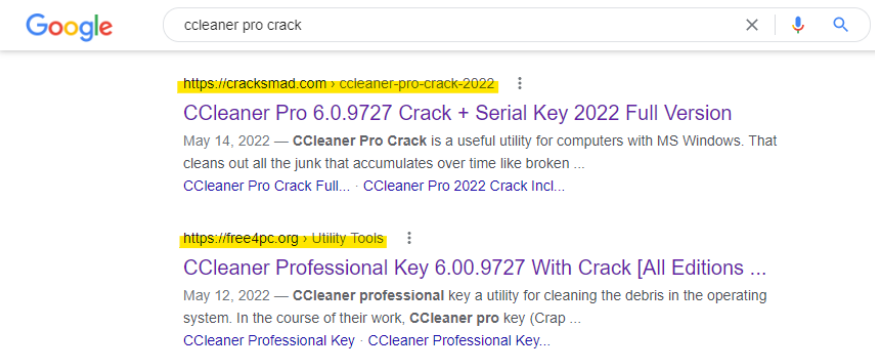
- Websites which lack web malware removal capabilities and doesn’t address website vulnerabilities remediated in timely manner would results in infection and compromise larger number of victims for larger users.
- Legitimate website which is doing the illegal activities to steal data and sell it for better profit.
The Deep Web
The area of the web that is not indexed or searchable by common search engines is known as the Deep Web.To locate and access a given website or service, users must log in or possess the required IP address or URL. Other pages are categorized as being on the Deep Web because search engines cannot index them since they do not use common top-level domains (TLDs), such as.com,.gov, and.edu. On the other hand, some pages actively prevent search engines from finding them.
Example Use cases:
- Websites that provide secret services or access to the specific people. This could be kind of some illegal services that is hosted in the data center and website URL cant be retrieved by search engines like Google , Yahoo , Bing , etc. Often times website admin disables index on robots.txt & disable SEO settings.
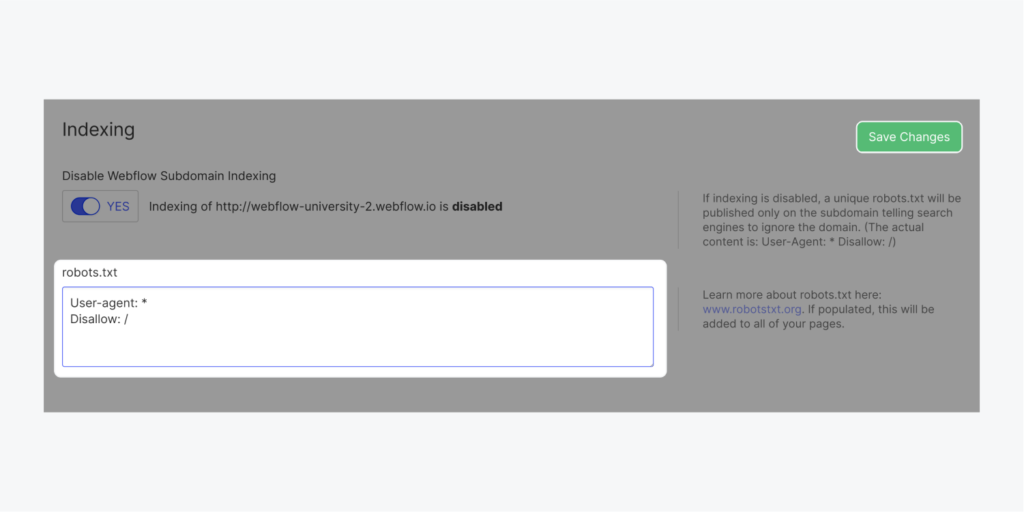
- Sample Robots.txt rules to populate the robots.txt file with specific conditions.
To hide your entire site
User-agent: *
Disallow: /
To hide individual pages
User-agent: *
Disallow: /page-name
To hide an entire folder of pages
User-agent: *
Disallow: /folder-name/
- Companies should purchase the best threat intelligence tools that can scrape off newly hosted Web sites that may pose a security risk to the organization.
The Dark Web
The Dark Web is a portion of the Deep Web that is harder to reach and relies on connections between reliable peers. It also requires specialist software, tools, or equipment to access.Tor and I2P are two prominent tools for this.
The easiest approach to find pages on the Dark Web after logging into Tor or I2P is to get a link from someone who is already familiar with the page.
Example Use cases:
- Due to media coverage of the Dark Web’s unlawful activity, it is well-known.The Dark Web is used by malicious actors to advertise, sell, and/or transmit unlawful goods and material, including malware, illegal weapons, drugs, and stolen data.
- But just like the Surface Web, there are a number of acceptable uses for the Dark Web as well, including information access, information sharing, identity protection, and interpersonal communication.The Dark Web is used by several news outlets to secure their sensitive sources.
Conclusion
In the end, intelligence obtained from a variety of sources, including the Surface Web , Deep Web and the Dark Web, enriches the field of CTI. To create a soundless, pertinent, and precise threat intelligence, it is necessary to leverage all-important sources and to combine gathered intelligence with data.



































